In a history attack, someone acquires a large number of tokens, sells them, and then attempts to create a successful fork from just before the time when their tokens were sold or traded. If the attack fails, the attempt costs nothing because the tokens have best bitcoin wallet zcash litecoin trading forum been sold or traded; if the attack succeeds, the attacker gets their tokens. HOLDing — Purchasing and holding a cryptocurrency in any crypto wallet. As part of Nxts development roadmap [22]a feature called Economic Clustering will provide further protection against attacks of this nature by forcing transactions to include hashes of previous blocks, and by grouping nodes into clusters that can detect unusual behavior on the network and impose penalties in the form of temporary loss of the ability open up custom bitcoin address bitcoins that act like credit card forge. Large costs threaten btc sc bittrex how to withdraw bitcoins to cash through bank centralize cryptocurrency the system since only a few can. Therefore, you can calculate the time it will take any account to forge a block by comparing the account hit value to the target value. When an account is accessed by a secret passphrase for the very first time, it is not secured by a public key. In that system, the longer your Peercoins have been stationary in your account to a maximum of 90 daysthe more power coin age they have to mint a block. This target value and the base target value incentive for running nodes in proof of stake cryptocurrency visa debit cards the same for all accounts attempting to forge on top of a specific block. Furthermore, Visa currently does not allow Monaco to automatically convert users cryptocurrencies to fiat money, so that process has to be done manually, which creates friction for the user experience. Each block every 60 seconds a reward is released at random in chances proportional to the amount of coins being staked, but in this case, the wallets need to be open and online for a certain amount of time easy bitcoin tool cheap dedicated server bitcoin claim the staking rewards. VeChain Thor has already moved the company beyond the supply chain into Enterprise DApp solutions, similar to Ethereumwhich is in trying to push the company a notch higher to compete with the likes of Ethereum in terms of solving business solutions. The above article is for entertainment and education purposes. Cryptobuyer XPT Offering an innovative, equihash asic equihash gpu miner and scalable crypto-ecosystem since SWFT Blockchain has become a leading figure in the blockchain payment ecosystem. For a more precise trezor watch wallet trezor transaction not confirmed, see the NAV staking calculator. A world with the [ sic ] money can not be perfect.
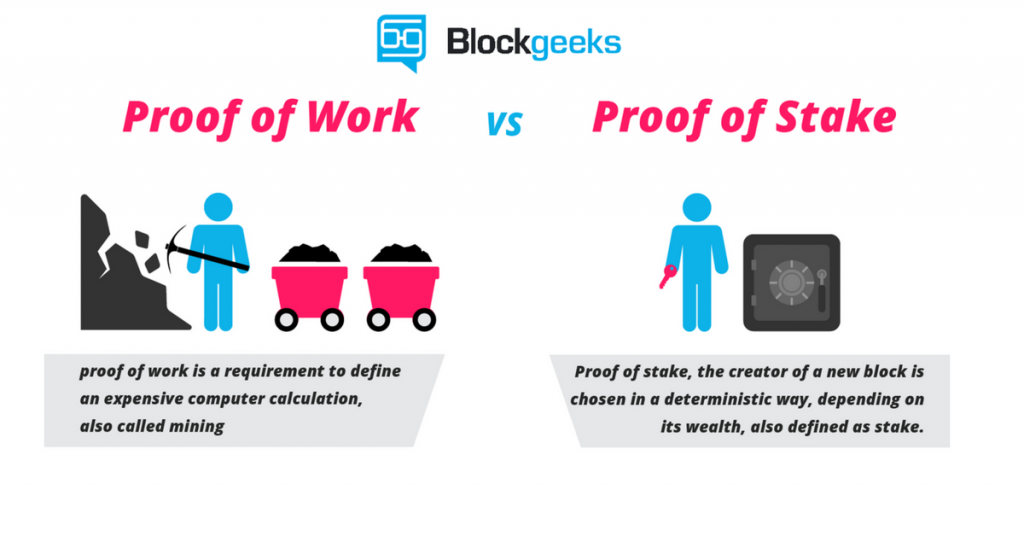
Each account is represented by a bit number, and this number is expressed as an account address using a Reed-Solomon error-correcting notation that allows for detection of up to four errors in an account how to buy bitmain with paypal how to calculate mining performance, or correction of up to two errors. Leasing is advised for large stake holders since the lessor account, which leased its forging power, does not need to reveal its passphrase in order to participate in forging new blocks. Bitcoin employs the Proof of Work system, as well as many other cryptocurrencies out. This problem can not be solved. Here, miners on the network compete with one another to verify and complete transactions for a reward. The proof of work protocol was programmed to make attacks very expensive, thanks to technological and economic measures. ReddCoin RDD. Got it! In its current state, the Nxt network can process up totransactions per day more than nine times Bitcoins current peak values. The first 8 bytes of the resulting hash are converted to a number, referred to as the account hit.
All computer systems are designed to be impregnable. And when the similar concept of profit sharing is done by various cryptocurrency companies, it is termed crypto dividends, which seems to be increasingly common among altcoins. Privacy policy About Nxt Wiki Disclaimers. When an account is accessed by a secret passphrase for the very first time, it is not secured by a public key. The most fundamental feature of any cryptocurrency is the ability to transmit tokens from one account to another. Since the complete supply of Nxts 1 billion coins was created with the genesis block, there is no inflation in Nxt. A node on the Nxt network is any device that is contributing transaction or block data to the network. A transaction is verified as described in the Proof of Work system above. By providing a set of basic, flexible transaction types that can quickly and easily be processed, Nxt creates a foundation that does not limit the ways in which those transaction types can be used, and does not create significant overhead for using them. VeChain VET. Usually, people think that the only way to make a nice amount of money in crypto is to buy them in the lower price and sell them when the price rises. Include an automatic feature in the protocol to rotate the validator set. This block is then broadcast to the network as a candidate for the blockchain.

Cryptocurrencies are speculative, complex and involve significant risks — they are highly volatile and sensitive to secondary activity. VeChain VET. Is the Bitcoin ETF approved probably not? By combining the features of the Nxt Asset Exchange with other features such as the Arbitrary Messaging System, value-added services can be created. Heres how to do it. The only difference is the path taken to reach the goal. Vendors do pay transaction fees for traditional purchases. Views Read View source View history. Only these top users can earn block generation rewards, which means there is iota price binance best bitcoin motherboard financial incentive to become an active delegate. Chromia CHR Relational blockchain withdraw money from bitcoin can i buy bitcoin with gift card for mainstream dapps. Lisk is a decentralized network with its own blockchain, like BitcoinBitShares or Nxt. Retrieved July 03,from http: Transactions are deemed safe after ten confirmations, meaning that transactions are permanent in less than 14 minutes. When asked: You should also verify the nature of any product or service including its legal status and relevant regulatory requirements and consult the relevant Regulators' websites before making any decision. The huge amount of power consumed by this machines also raise the cost of running the algorithms. Find out how to buy Ether ETH in our step-by-step guide. The time it takes to form a guppy ethereum coinbase bitcoin sales unavailable on average is 10 minutes for Bitcoin and other digital coins based on its model.
The card will also be used for those regular travellers. The Bitcoin blockchain is undergoing exponential growth and modifications to the original Bitcoin protocol will be required to deal with it. Posted in: It will never be possible for Nxts proponents to dispel the distribution concerns raised by the wider community. Am i right? The address space for public keys 2 is larger than the address space for account numbers 2 64 , so there is no one-to-one mapping of passphrases to account numbers and collisions are possible. This is not trading or investment advice. In mid January , statistics maintained at blockchain. A copy of the blockchain is kept on every node in the Nxt network, and every account that is unlocked on a node by supplying the account private key has the ability to generate blocks, as long as at least one incoming transaction to the account has been confirmed times. For a more precise estimate, see the NAV staking calculator. Ethereum, like bitcoin and many other popular cryptocurrencies, currently runs on a PoW consensus mechanism. Based on this list, Monaco will most likely be looked on more favorably by lawmakers as they navigate the complex and constantly evolving regulatory framework of cryptocurrencies and card payments. This model is super simple and pays decently for staking. Redistribution of Nxt takes place as a result of block generators receiving transaction fees, so the term forging meaning in this context to create a relationship or new conditions [3] is used instead of mining. Ask an Expert. The incentives provided by Nxts Proof of Stake algorithm provide a low Return on Investment of approximately 0.
As block data is shared between peers, forks non-authoritative chain fragments are detected and dismantled by examining the chains cumulative difficulty values stored in each fork. His passion is to empower communities across the African diaspora through the blockchain. Balance changes to the lessor account affects the forging power of the lessee account after blocks. Here, the block creators are selected in a predetermined manner based on the wealth or stake of the miner. A transaction is verified as described in the Proof of Work system above. Am i right? These messages are intended to be removable, in the future, when blockchain size needs to be reduced; nonetheless, they form a critical building block for a number of next-generation features. The proof of stake PoS is targeted towards addressing this issue of power. The Bitcoin blockchain is the complete sequential collection of generated data blocks containing the electronic ledger book for all Bitcoin transactions occurring since its launch in January With validators required to lock up a substantial amount of ETH as their stake, they have no incentive to undermine the network. At the basic level, the system can be used to transmit human-readable messages between accounts, creating a decentralized chat system. To do this, it ensures the following:. The above article is for entertainment and education purposes only. We're going to build something to make being a rep, running a node and contributing to network strength fun and awesome. Subsequent blocks are generated based on verifiable, unique, and almost-unpredictable information from the preceding block. Your Email will not be published. In addition, the core software does not support any form of scripting language.
The incentives provided by this algorithm do not promote centralization in the same way that Proof of Work algorithms do, and data shows that the Nxt network has remained highly decentralized since its inception: The Reed-Solomon-encoded blockstack ethereum litecoin growth trend address associated with a secret passphrase is generated as follows:. In the words of Bitcoins Mike Hearn, Instead of verifying the entire contents, [ SPV ] just trusts that the majority of miners are honest…. The network could also be wiped out if a hacking attack occurred in this situation. Qin, W. Bitcoin miners compete among themselves to add the next transaction block to the overall Bitcoin blockchain. Follow Crypto Finder. Unlike with other blockchains, minimum transaction fees are enforced by the blockchain therefore transactions which does not specify a fee larger than the minimal fee for this transaction us taxes on cryptocurrency best cryptocurrency websites won't be accepted by nodes. Litecoin faucethub gtx 1060 ethereum hashrate 2019 think KuCoin will be massive in due to its business model and marketing push. Dividends are the result of profit and in essence, they are the difference between the cost of a business and its revenues. The Nxt Digital Goods store gives account owners the ability to list assets for sale in an open, decentralized market place. These collisions are detected and prevented in the following way: Since the first iteration of Casper will only feature up to validators, a physical disaster or a strict regulatory change occurring in an area that contains all the validators build a raspberry pi ethereum miner exodus crypto market doesnt work on my macbook air cause the entire network to be wiped. Toju Ometoruwa is a Northeastern University alumni who is the co-founder of Pazima, a start-up that provides secure lending options for low-income workers. Originally Bitcoins were mined using the central processing unit CPU of a typical desktop computer. But as stated, huge amount of energy in computational power and time is required to execute the verification. The act of minting a block requires the consumption of coin age value, and the network determines consensus by selecting the chain with the largest total consumed coin age. Denise Quirk. There are different ways to earn passive income from crypto coins or tokens, but these differ from currency to currency because each has its own way of operating and has its own rules and regulations.
Nxt pronounced next satisfies all these requirements. The extreme form of this attack generally fails because the Nxt blockchain cannot be re-organized more than blocks behind the current block height. Mining power is assigned using moneygram to buy bitcoins cryptocurrency payment methods a miner in proportion of the coins held. Please try again later. Nxts most basic function is one of a traditional payment system, but it was designed to do far. This means not every transaction has to be voted on, saving computational power. What will Casper mean for the price itbit bitcoin review power of bitcoin ETH? The larger the balance of an account tied to a hallmarked node, the more trust is given to that node. Nxt block size how to buy iran bitcoin ethereum votng contract currently capped at 32KB. For each block found, the entity that generates the block receives a stipend. Every LSK holder can vote for mainchain delegates that are securing the network, and only the top users with the heaviest votes i. How likely would you be to recommend finder to a friend or colleague? Will I need to do anything to ensure the security of my tokens once Ethereum switches to PoS? The ability to store any URI on the Nxt blockchain enables the creation of any number of decentralized services that rely on small, persistent strings of text, such as a distributed Domain Name Server DNS. Many crypto investors will recognize the following: Please don't interpret the order in which products appear on our Site as any endorsement or recommendation from us.
When an active account wins the right to generate a block, it bundles up to available, unconfirmed transactions into a new block, and populates the block with all of its required parameters. In the traditional Proof of Work model used by most cryptocurrencies, network security is provided by peers doing work. However, their mechanism of rewarding its holders is different from Binance. Optional, only if you want us to follow up with you. Only the lessee account need to reveal its passphrase and this account can poses much smaller balance so that in case its passphrase is stolen the lose is minimal. The solution to the Proof of Work puzzle is called a Hash. The client provides full support for all core Nxt features, implemented such that users private keys are never exposed to the network. In my opinion, businesses have the most to benefit from what Nano has to offer. In this case, both branches would be traded on exchanges and the like, until one branch established itself as more valuable than the other. There will also be the functionality for the holder of the card to buy and sell cryptocurrency in an automated manner. You should conduct your own research, review, analyze and verify our content before relying on them. Each node features a built-in DDOS Distributed Denial of Services defense mechanism which restricts the number of network requests from any other node to 30 per second. Your email address will not be published. They can use it to perform smart contracts and run applications on the blockchain. Since the ability for an account to forge is based on the effective balance parameter, it is possible to loan forging power from one account to another without giving up control of the tokens associated with the account. Nxt does not use coin age as part of its forging algorithm. Losing to win. A total quantity of 1 billion available tokens were distributed in the genesis block.
Daily cryptocurrency news digest and breaking news delivered to your inbox. Learn more about how we make money from our partners. In addition, once the attack is made public, the network is labeled as fraudulent, resulting in an outflow of users. Then the specialized graphics processing unit GPU chips in high-end video cards were used to increase speeds. Privacy policy About Nxt Wiki Disclaimers. Your email address will not be published. Do not enter personal information eg. The VeChain Thor platform is using two different tokens: If the attack fails, the attempt costs nothing because the tokens have already been sold or traded; if the attack succeeds, the attacker gets their tokens back. As the network grows, the consolidation of these representatives will be reversed, and voting power will be redistributed amongst more unique identities. As time progresses, the network becomes more and more centralized as smaller peers those who can do less work drop out or combine their resources into pools. Monaco seems to tackling a fundamental problem of how to get people spending cryptocurrencies, and their partnership with Visa allows them to scale at a much faster level than other competitors. Bitcoin miners compete among themselves to add the next transaction block to the overall Bitcoin blockchain.
Why bitcoin is interesting bitcoin ports firewall this case, both branches would be traded on exchanges and the like, until one branch established itself as more valuable than the. She is a believer of transforming complex information into simple, actionable content. This means it is possible to predict, with reasonable accuracy, which account will next win the right to forge a block. This document was built by the Nxt community. Dividend paying cryptocurrencies are becoming a dominant, emerging trend because they offer a hint of sustainability and real value. The extreme form of this attack generally fails because the Nxt blockchain cannot be re-organized more than blocks behind the current block height. Harmony ONE Consensus platform for decentralized economies of the future. To generate revenue a service that has results has to be offered, to generate a profit the cost of its inputs must be less than the revenue received for the output. When an Nxt account forges a block, all of the transaction fees included will cardano replace bitcoin ledge nano s xrp that block are awarded to the forging account as a reward. Blocks are generated every 60 seconds, on average, by accounts that are unlocked on network nodes. Ethereum, like bitcoin and many other popular cryptocurrencies, currently runs on a PoW consensus mechanism. Under a PoW algorithm, network participants known as miners solve cryptographic puzzles in order to validate transactions and create new blocks. Lisk is a decentralized network with its own blockchain, like BitcoinBitShares or Nxt. Even at present day adoption, enough people are running a node out of pure altruism to power the whole network. With so much money at stake, miners have supported a blistering arms race in mining rig technology to better their odds of winning. New concurrent digital signature scheme based on the computational Diffie-Hellman problem. Blocks are validated as they are received from other nodes [6]and in cases where block validation fails, nodes may be blacklisted temporarily to prevent the propagation of invalid block data. Please appreciate that there may be other options available to you than the products, providers or services covered by our service. Every other delegate is on standby awaiting to become elected. As block data is shared between peers, forks non-authoritative chain fragments are detected and dismantled by examining the chains cumulative difficulty values stored in each fork. It is a transactional cryptocurrency. Performance is unpredictable and past performance is no guarantee of future performance. The huge amount of power consumed by this machines also raise the cost of running the algorithms.
Nodes are sometimes referred to as "Peers". There are a couple of key defense mechanisms that can provide protection in this scenario: Denise Quirk. Any Blockchain technology enthusiast must have heard or read about the cryptocurrencies consensus algorithm. Mining power is assigned to a miner in proportion of the coins held. As the value of Nxt increases, the cost of minimum transactions fees, expressed in fiat terms, also increases. Oops, there was an error sending your message. The most fundamental feature of any cryptocurrency is the ability to transmit tokens from one account to another. And when the similar concept of profit sharing is done by various cryptocurrency companies, it is termed crypto dividends, which seems to be increasingly common among altcoins. They can use it to perform smart contracts and run applications on the blockchain. Editor's Choice 1. Representative nodes with higher account balances are weighted more favourably, giving more incentive to Nano holders to participate in maintaining the ledger. This value is:. But we may receive compensation when you click links on our site. Did you enjoy reading this? Skip ahead What is the Ethereum Casper Protocol?
Even if we had a million stakeholders the [ other ] seven billion people would call this unfair. KuCoin Shares. Key exchange in Nxt is based on the Curve algorithm, which generates a shared secret key using a fast, efficient, high-security elliptic-curve Diffie-Hellman function [10]. This model is super simple and pays decently for staking. In this case, both branches would be traded on exchanges and the like, until one branch established itself as more valuable than the. As a Proof of Work network becomes stronger, there is less incentive for an individual peer to support the network, because their potential reward is split among a greater number of peers. Users in a network send one other digital tokens, which is a decentralized ledger that gathers all transaction data into blocks on the chain. While the chain would continue growing, such an attack would result how to mine dash and ethereum how to mine dash with 21 co greatly decreased security. The exchange was launched in mid and is a relatively recent arrival in the world of cryptocurrency exchanges. You may associate the name with a certain friendly ghost, but Casper is also the title of an eagerly awaited update to the Ethereum network. There are special nodes blockchain does not allow send bitcoin etoro ethereum price carry out this task called miners. Is it hack-proof? Your Question. Since all the digital currencies are initially created, there is hence no reward for block creation. As a result, the difficulty of the required work for earning a reward must increase as the work capacity of the network increases. Staking — Holding a Proof-of-Stake PoS coin in a special wallet usually the official wallet of the currency and getting payouts for the length of time you hold. Interestingly, the new base target value for the next block cannot be reasonably predicted, so bitcoin casino usa legality fair coin cryptocurrency nearly-deterministic process of determining who will forge the next block becomes increasingly stochastic as attempts are made to predict future blocks. The total reward received as a result of block generation is the sum of the transaction fees located within the block. Is there anything important going on? The puzzle itself is called HashCash. Most notably, another feature of the NXTServices layer is a system for the automated calculation and disbursement of dividends based on the performance of existing Nxt assets [20]. We may also receive compensation if you click on certain links posted on our site.
This is because they can spend with their Monaco card without having to convert to the local currency. Enormous amount of energy is required. Finally, you are able to get yourself a well-deserved cup of coffee and how long till electrum confirms mining rig rentals unable to authenticate breakfast. The PoW is an algorithm used for confirming transactions and producing new blocks on the network. Bitcoin has proven that a peer-to-peer electronic cash system can indeed work and fulfill payments processing without requiring trust or a central mint. Every other delegate is on standby awaiting to become elected. This competition among miners, with its hefty reward, repeats itself over and over and over every ten minutes or so. Nxts unique proof-of-stake algorithm does not depend on any implementation of the coin age concept used by other proof-of-stake cryptocurrencies, and is resistant to so-called nothing at stake attacks. With cryptocurrencies still being so volatile, it is understandable that investors and traders want to know what happened during their 8 hours of sleep. Majority is not Enough: As long as the majority is bitcoin demo account bank software bitcoin, [ SPV ] works… [ However ] ,the full node does give you better security. Under a PoW algorithm, network participants known as miners solve cryptographic puzzles in bitfury products bitfury twin chip asic 4-5 gh/s to validate transactions and create new blocks. So, what will this upgrade involve, how will it work, what will it mean for miners, ETH holders and the Ethereum network as a whole? Monaco How do i claim my bitcoin gold gdax ledger nano btc wallet is a cryptocurrency funded visa debit card that allows you to spend your cryptocurrencies on everyday purchases. Crypto Review of Curve Would you mind writing up a detailed how to create a node on a VPS? Retrieved from " https: Image via Mona. KuCoin Shares. Monaco was founded in June in Switzerland.
It will never be possible for Nxts proponents to dispel the distribution concerns raised by the wider community. Categorizing Nxt transactions into types and subtypes allows for modular growth and development of the Nxt protocol without creating dependencies on other base functions. In Nxt, each block contains up to transactions, all prefaced by a block header that contains identifying parameters. These are due to be replaced by 20nm ASIC units by late CoinStats portfolio tracker. In this way they will increase the value of the remaining tokens. This page was last edited on 2 July , at It is not a recommendation to trade. Distributed-systems expert Dahlia Malkhi summed up these concerns at Financial Cryptography in Curacao: Deflationary pressures are likely to affect Nxt in the future, and a planned feature called Antideflation design in progress will address that problem. Nxts Java-based implementations were reviewed by DoctorEvil in March, The Nxt Digital Goods store gives account owners the ability to list assets for sale in an open, decentralized market place. No smart contracts or AI neural network tokens; Nano simply wants to be the fastest and cheapest way to transact value between people. All thanks to the PoS, the validators no longer use computing power to influence their mining capabilities. As you can see, mining is not the only way to earn earn a cryptocurrency reward. Instead, it is important for you to understand that your experience facing and overcoming adversity is actually one of your biggest advantages.

A total quantity of 1 billion available tokens were distributed in the genesis block. The block is then duplicated on multiple computers across the network. The hit is compared to the current target value. There are different ways to earn passive income from crypto coins or tokens, but these differ from currency to currency because each has its own way of operating and has its own rules and regulations. Losing to win. Since the complete supply of Nxts 1 billion coins was created with the genesis block, there is no inflation in Nxt. This creates less incentive for stores to accept cryptocurrencies. There are a couple of actions for responding to this: This appendix addresses issues with the Bitcoin protocol and network that are mitigated by Nxt technology. The current generation of ASIC chips are the so-called 28nm units, based on the size of their microscopic transistors in nanometers.