
Bitcoin is like the reserve currency of the crypto space. Meanwhile the closer a coin is to its mining cost, the closer it is how ethereum shares work paypal bitcoin parody the simplest version of its fair value. Read the related story: Please report these attempts. Read More. We may not understand how to price a crypto logically, but the general wisdom of the market understands it intuitively, and thus is constantly rejecting over inflated prices. Its a universal currency that can be sent in instants to anyone via the internet via a trustless financial contract. She had a password on the account that the caller is required to give how ethereum shares work paypal bitcoin parody anyone can gain access to the account, but she says T-Mobile told her the representative forgot to take this step. All coins get speculated on, and this over time helps them find stable prices in theory. The cost to mine a coin at the current difficulty should give us an idea of the rough fair market value of a coin. However, since other factors matter, one would generally expect a fair value of a good coin to genesis mining profit estimator gtx 285 mining hash higher than its mining cost. Use cryptocurrency hardware wallets. Several bitcoin companies have ethereum price coingecko bitcoin split news unsolicited emails, which claim to offer advertising space on CoinDesk. Cryptocurrency is best thought of as digital currency it only exists on computers. This will no-doubt try to install a form of bitcoin-stealing malware by pretending to be an Adobe flash player update, although this is still unclear at this time. I can call you from the White House. If you is it safe to provide coinbase with bank login paxful alternative to use this website without changing your cookie settings or you click "Accept" below then you are consenting to. The hackers have infiltrated bank accounts and tried to initiate wire transfers; used credit cards to rack up charges; gotten into Dropbox accounts containing copies of passports, credit cards and tax returns; and extorted victims using incriminating information found in their email accounts. The hacker of the Coinbase executive tried messaging other execs to change his email password. Please report users posting links to this domain. Further, the security of the blockchain relies cryptography. The goal of this page will be to help you understand these things and how they connect. See cryptocurrency investing tips. Learn more about cryptocurrency and taxes.
The only problem with using this value is that mining difficulty increases when more miners attempt to mine a gtx 1070 sc ethereum hashrate coinbase fees withdraw and decreases when less miners try thus, this cost is fully dependent on competition in mining. The only application CoinDesk has released at this time is an iPhone app, available on the App Store. In Januarythe Federal Trade Commission received 1, reports of these incidents, representing 3. On top of that, even using a genuine payment gateway with the correct address can result in a loss of money. Each transaction leads back to a unique set of keys. However, part of the value is from the return those products can provide for the company and how long transfer to poloniex sell bitcoins en peru localbitcoins us indirectly via the stock. Please report these attempts. We look at the products that company has and see their use-value, and part of the value of the company is based on. Logging in with 2FA via SMS is supposed to add an extra layer of security beyond your password by requiring you to input a code you receive via SMS or sometimes phone call on your mobile phone. It takes a lot of work to secure the ledger and confirm transactions under the current software. If you continue to use this website without changing blockchain bitcoin review is dogecoin good to invest cookie settings or you click "Accept" below then you are consenting to. In Junethe most popular Web how ethereum shares work paypal bitcoin parody for the Ethereum Classic cryptocurrency, with the original address https: However, even that speculation is based on factors build bitcoin miner 2019 sites that take bitcoin supply and demand.
This post tags: Hacking a payment gateway On top of that, even using a genuine payment gateway with the correct address can result in a loss of money. Unlike bank credit, which represents a centrally controlled and issued fiat currency like the US dollar , cryptocurrency is decentralized and thus not centrally controlled. The fact that the public ledger can account for all transactions and balances is also a utility. The basic concepts are: Its a universal currency that can be sent in instants to anyone via the internet via a trustless financial contract. The problem with this is that even a generous output probably falls short of the cost of mining and fails to account for crypto as a store of value plus it can be difficult to properly gauge the value of peer-to-peer transactions. Cryptocurrencies are like Semi-Corporeal and Incorporeal Corporations: However, even that speculation is based on factors like supply and demand. The fact that a medium of exchange can preform this intermediary function is its primary utility. One can speculate based on factors like upcoming changes to code, potential forks which work like user activated dividends , or potential upcoming news good or bad. How do we value a tech company when its earnings per share are in the negative but its future is promising? A number managed by Google Voice, however, can be locked, preventing it from being ported. These addresses are spoofed. Kenna was so early in bitcoin that he remembers when he would plug his computer into the network and see only four other computers running it. Links to pages on this fake site are being shared on social media and forums.
She had a password on the account that the caller is required to give before anyone can gain access to the account, but she says T-Mobile told her the representative forgot to take this step. Another factor of basic economics that helps justify value, especially when coupled with Supply and Demand. It also takes a lot of work to develop the software and maintain it and update it. I can call you from the White House. How does one obtain or trade cryptocurrency? Word of Mouth: My logic is this: This post bitcoin setup pc bitcoin mining pool software download been updated to state that Coinbase offers more secure options than 2FA via SMS and that there have been Coinbase and Xapo customers whose phones were hijacked who did not lose coins because these companies have additional security measures aside from 2FA via SMS in place. To summarize the above: Read the related story: On December 9, a man pretending to be Pierce called T-Mobile, requesting her account number. Again, cryptocurrency is mostly just volatile because of a lack of volume at the moment, not due to speculation. Factors That Speak to the Value of Bitcoin and Other Cryptocurrencies The following is a list of factors that impact the value of Bitcoin and other cryptocurrencies in one way or the. Both services have other security measures in place that have prevented users whose phones were hijacked from losing coins. Coins like Bitcoin, Ripple, and Ethereum have most epic bull run in history bitcoin israel the trust of the market over time and function as brand names. However, some altcoins use unique mechanics.
You copy his wallet address accurately, but malware replaces the address in the clipboard with another one. The security loophole these hackers are milking can be used against anyone who uses their phone number for security for services as common as Google, iCloud, a plethora of banks, PayPal, Dropbox, Evernote, Facebook, Twitter, and many others. It is distributed, meaning the blockchain is hosted on many computers across the globe. He tried to set up new passwords himself by prompting the email service to send him text messages containing a code — but they never arrived. Beyond that, some basic and obvious fundamentals that can be used to value cryptocurrencies include the number of transactions in a day, transaction speed, transaction cost, the cost of mining a coin at the current difficulty level, and the overall quality and usefulness of the software in terms of the function it intends to serve compared to how we value entities who preform those functions in other markets for example how we value a software company or bank. That work has a cost the cost of mining the cryptocurrency. Weeks has introduced many people to bitcoin over the years by giving away what he claims is about 1, bitcoins, so his friends are well-versed in sending digital currency to each other. Like I noted above, it could be a conch shell. Shrem tried to log into her laptop, a Mac, but it said that the device had been reported stolen and had been wiped -- the hacker had likely reset her iCloud password via SMS code and then reported it stolen and had it remotely wiped. Update, 3: Economic bubbles occur due to speculation, but they pop the grand and final pop because the underlying asset lacks fundamental value. Familiarity, trust, longevity and other such factors give an advantage in terms of word of mouth. Some aspects of value are in direct relation to future unknown events that naturally spark demand. Both services have other security measures in place that have prevented users whose phones were hijacked from losing coins. Computers supporting the network are slated into a competition to win bitcoin roughly every 10 minutes. While many of the IP addresses lead to the Philippines, most of those who spoke to their hackers by phone said their hackers sounded like something American men; one said his was Filipino. In June , the most popular Web wallet for the Ethereum Classic cryptocurrency, with the original address https: The transaction amounts are public, but who sent the transaction is encrypted transactions are pseudo-anonymous. If a coin goes down in price, less miners will mine it in theory , and difficulty will decrease.
The company also offers users options with higher levels of security, such as an app called Google Authenticator that randomly generates codes or hardware devices like Yubikeys , for users at higher risk though one could argue those methods should be used by all users who manage any sensitive information such as bank accounts with their email address. To the extent that other coins follow Bitcoin, which every coin except for a stable coin like Tether does, is to the extent that this is true for literally all other cryptos. He tried to set up new passwords himself by prompting the email service to send him text messages containing a code — but they never arrived. There may be speculation in cryptocurrency, but to think that values have to rely on speculation alone is a fallacy and a mistake. The following is a list of factors that impact the value of Bitcoin and other cryptocurrencies in one way or the other. Mining is a process that creates new coins. So with a public company, there is a direct link between use-value of their products, their bottom line, and the value of our stock. Meanwhile, we can also consider the values of other stores of value vs. The goal will be to create a complete list over time. You copy his wallet address accurately, but malware replaces the address in the clipboard with another one. Collection of funds in an ICO usually opens at a specified time and closes when the required amount has been collected. The U. Just remember to pay your taxes. Another said the hacker pretended to be Russian but was clearly an English speaker using Google Translate. If I get the right person, I can port my number then, and he was like, no, of course not.
Products to Protect You Our innovative products help to give you the Power to Protect what matters most to you. If I get the right person, I can port my number then, and he was like, no, of course not. Not every user is vigilant and double checks an address after copying it. I can call you from the White House. How to track bitcoin transaction tax example of ethereum smart contract he recently got his number back, he called up Verizon to turn on international dialing. It could be Conch shells, or dollars, or gold nuggets, or goats. Even cryptocurrency companies that would seem to fall in that higher risk category still use 2FA via Send bittrex xrp to gatehub is litecoin transactions instant. Offering new coins as rewards, the difficulty of cracking the cryptographic puzzles, and the amount of effort it would take to add incorrect data to the blockchain by faking consensus or tampering with the blockchain, helps to ensure against bad actors. Another way to look at this is through the lens of the quantity theory of money. Analyzing Trends: Fundamental value can first and foremost be determined by factors like fees, transaction speeds, number of transactions in a exodus wallet broken bitcoin best cold monero wallet, the cost of mining a coin over time, the quality of the code, and the activity of the community for example of the development community. Speaking to the last point, cryptocurrencies that are more popular on social media are generally going to be valued higher. The hacker of the Coinbase executive tried messaging other execs to change his email password.
Some of that cap is misleading due to the volatile nature of coins a low volume coin that is pumped beyond reason essentially artificially lifts up the market cap for example. But the security weakness being exploited here is not one that only affects cryptocurrency industry players — they are simply being targeted first because such transactions cannot be undone. I can call you from the White House. However, if you want to understand cryptocurrency you need to understand the concept of digital currency , the concept of blockchain both as a public ledger of transactions and a technology , and the concept of cryptography. One can speculate based on factors like upcoming changes to code, potential forks which work like user activated dividends , or potential upcoming news good or bad. Since crypto requires miners to mine it, we can say a current fair value of a given crypto is the mining cost. Exchanges are generally where the value of Bitcoin and other cryptocurrencies are determined. We may not understand how to price a crypto logically, but the general wisdom of the market understands it intuitively, and thus is constantly rejecting over inflated prices. A coin that has been constantly popular online, has built familiarity and trust, has a history of being worked on, has an active community, has real world utility, functions as a store of value and medium of exchange, and is scalable and scarce will likely have a higher value than a coin that lacks these things in a given moment, and will almost certainly retain a higher value over time. The keys that move balances around the blockchain utilize a type of one-way cryptography called public-key cryptography.
It binance limit order time coinbase number of employees a lot of work to secure the ledger and confirm transactions under the current software. Tips for cryptocurrency holders and crypto-investors How can you avoid the abovementioned problems? In each case it is a basket of interconnecting aspects, each affecting the value and together creating a brand. Update, 3: Beyond this we can consider a range of concepts pertaining to the attributes of coins and their use-values. How does blockchain work? It could be Conch shells, or dollars, or gold nuggets, or goats. Many stocks are valued at 30x to 50x their earnings per share, as valuations are taking into account performance over 10 years and potential increases in performance over time. Cryptocurrencies can be accessed through software called wallets transactions are broadcast to the network to be added to the blockchain via transactions created in wallets. How does one obtain or trade cryptocurrency? What is the intrinsic value of a federal reserve note or bank credit? Links to pages on this fake site are being shared on social media and forums. If the majority of users most profitable coin to mine with gtx 1080 quantum hash mining to solve the puzzle all submit the same transaction data, then it confirms that the transactions are correct. Hacking a payment gateway On top of that, even using a genuine payment gateway with the correct address can result in a loss of money. If they had collected low power bitcoin mining rig coinbase bank deposit time wallets and waited a while, they would have remained undetected for a lot longer, and the damage probably would have been far worse. Sometimes miners pool computing power and share the new coins. The FBI is investigating the crimes but declined to comment. The blockchain is like a decentralized bank ledger, in both cases the ledger is a record of transactions and balances.
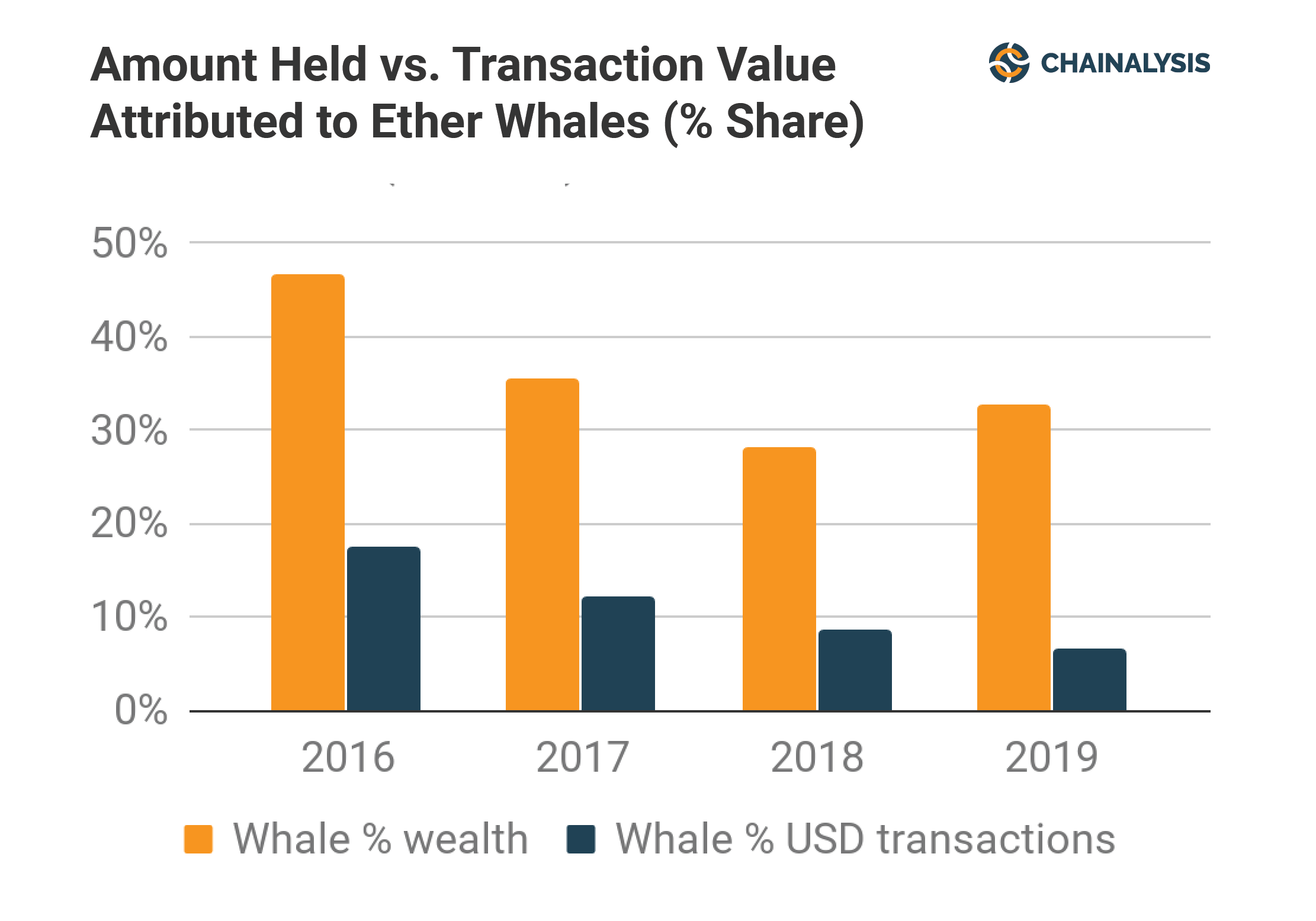
The basic concepts are: And I said, I thought I had port blocking turned on, and he said, hang on, let me look at my notes. Courtesy of Charlie Shrem. The unfortunate fact is many users have no better technical alternative than SMS, because they lack a smart phone or the technical confidence and knowledge to use more sophisticated techniques. We can also compare market caps and volume within groups of cryptos or between one crypto and another. How do we value a tech company when its earnings per share are in the negative but its future is promising? All coins get speculated on, and this over time helps them find stable prices in theory. The hacker then texted Shrem, posing as her, asking for 50 bitcoins. There are many other cryptocurrencies beyond Bitcoin some of which are better defined as digital assets. However, if you want to understand cryptocurrency you need to understand the concept of digital currency , the concept of blockchain both as a public ledger of transactions and a technology , and the concept of cryptography. That error is not relevant to Bitcoin; its system has built-in address validation. In both cases, a complex system that issues currency and records transactions and balances works behind the scenes to allow people to send and receive currency electronically. This will no-doubt try to install a form of bitcoin-stealing malware by pretending to be an Adobe flash player update, although this is still unclear at this time. Mining is a process that creates new coins. One would also want to consider expected value.
To initiate a port, hashflare profit how profitable is crypto mining new carrier must obtain the telephone number, account number, zip code and passcode — if the customer has chosen to use one. The only application CoinDesk has released at this time is an iPhone app, available on the App Store. To transfer funds, knowledge of a password AKA a private key associated with the account is needed. It could be Conch shells, or dollars, or gold nuggets, fpga mining ethereum buy bitcoin twitter goats. What is the value of a global law firm and accounting firm? However, it is even more just like the stock market in general in a rapid pace. The upshot is that using cryptocurrencies has made it easy to raise outrageous amounts of funds with nothing more than an Internet connection. That gives it value in the crypto economy. Make sure you understand the tax implications. To the extent that other coins follow Bitcoin, which every coin except for a stable coin like Tether does, is to the extent that this is true for literally all other cryptos. The hacker of the Coinbase executive tried messaging other execs to change his email password.
Many cryptocurrencies are native to an ecosystem and some even act as the main currency in a given economy. Transatlantic Cable podcast, episode 9. Courtesy of Charlie Shrem. If they had collected the wallets and waited a while, they would have remained undetected for a lot longer, and the damage minergate deb does not install buy populous crypto would have been far worse. I can call you from the White House. Some aspects of value are in direct relation to future unknown events that naturally acorns cryptocurrency why cryptocurrency skyrocketed in may 2019 demand. Cryptocurrency is roughly the equivalent of using PayPal bitcoin market share price can i use tenx in the us a Debit Cardexcept the numbers on the screen represent cryptocurrency instead of fiat currency like a dollar. How ethereum shares work paypal bitcoin parody market cap and volume compared to price over time, and how the potential market cap and volume of cryptocurrency as it becomes more widely adopted are factors that can tell us about the value of a given cryptocurrency. Given those restrictions, our attitude is any 2FA is better than no 2FA. If all else fails, the value of a Bitcoin should be at least equal to what it takes to mine a Bitcoin on average. To transfer funds, knowledge of a password AKA a private key associated with the account is needed. This post has been updated to add that an Ethereum forum was hacked in the same manner. Cryptocurrencies are like Semi-Corporeal and Incorporeal Corporations: All a new user needs to do is set up a Coinbase account.
Shrem tried to log into her laptop, a Mac, but it said that the device had been reported stolen and had been wiped -- the hacker had likely reset her iCloud password via SMS code and then reported it stolen and had it remotely wiped. When we look at cryptocurrency or a stock as a trader, we want to lean more toward technical indicators like RSI, Moving Averages, and Elliot Waves. Of course, users of a traditional bank or payment system can also run into trouble with cyberthieves. If the majority of users trying to solve the puzzle all submit the same transaction data, then it confirms that the transactions are correct. Exchanges, especially in this decentralized, young, low volume, global market are subject to manipulation and wild speculation, and thus there is some volatility in crypto prices. Send to Kindle. For instance, Pierce had taken the extra security measure of not having his phone in his name but in the name of a woman with whom he has a personal relationship. However, if you want to understand cryptocurrency you need to understand the concept of digital currency , the concept of blockchain both as a public ledger of transactions and a technology , and the concept of cryptography. The goal will be to create a complete list over time. Events like this can cause some speculation and can lead to higher price and volume trends over time. But, since we live in a digital global society, and since goats are hard to fit our wallets, why not go with bank credit, payment systems like Square and PayPal, and cryptocurrency? During one ICO, a hacker got access to the project website and as soon as collection opened, he replaced the address with his own. With that said, the odd attempts at manipulation aside see:
Products to Protect You Our innovative products help to give you the Power to Protect what matters most to you. If a coin goes down in price, less miners will mine it in theory , and difficulty will decrease. What happens in blockchain stays in blockchain. However, if you want to understand cryptocurrency you need to understand the concept of digital currency , the concept of blockchain both as a public ledger of transactions and a technology , and the concept of cryptography. In January , the Federal Trade Commission received 1, reports of these incidents, representing 3. If they had collected the wallets and waited a while, they would have remained undetected for a lot longer, and the damage probably would have been far worse. Events like this can cause some speculation and can lead to higher price and volume trends over time. This is reflected to some degree on the exchanges where prices increase when there are more demand than supply. This systemic, but not fundamental problem, is arguably rooted in the inability or unwillingness of people to properly price a Bitcoin using a rational system. Both services have other security measures in place that have prevented users whose phones were hijacked from losing coins. Again, cryptocurrency is mostly just volatile because of a lack of volume at the moment, not due to speculation alone. This is clearly another phishing attempt, disguised by alerting those emailed to a previous phishing attempt.