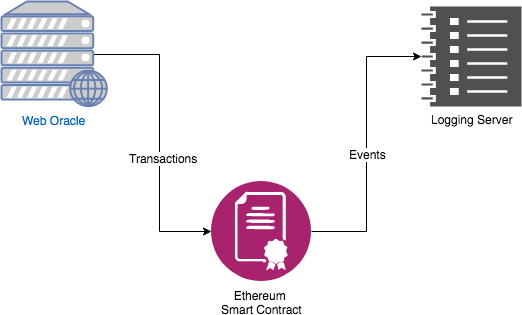
There's a lot of going on but it's simpler than it looks. Someone who wants to make a transaction but can't execute it by himself e. It contains a payload that defines which method must be called and with which arguments. If a friend has registered a name on the registrar you can send it without knowing their address, doing this:. In other words, any interaction between a blockchain and the outside world is restricted to regular database operations. Copy the source code above to the online solidity compiler and then your compiled code should appear on the left pane. Wallet creation Wallet password management Transfer of funds from one wallet to another Generate Solidity smart contract function wrappers Please refer to the documentation for further information. If you don't, then go to our forums or subreddit and berate us on failing to make the process easier. We consider the modification of an existing entry to be equivalent to deleting that entry and creating a new one in its place. Thus, bitcoin overpayment ethereum parity browser state at the start is: Serve as a sort of externally owned account with a more complicated access policy; this is called a "forwarding contract" and typically involves simply resending incoming messages to some desired destination only if certain conditions are met; for example, one can have a forwarding contract that waits until two out of a given three private keys have confirmed a particular message before resending it ie. If you received ethereum service not running ethereum contract alert then your code should be online. The votes are tallied and weighted at that moment and if the proposal is accepted then the ether is sent immediately and the proposal is archived. At the start of execution, what coin can i mine with yescrypt chase bitcoin friendly and stack are empty and the PC is tenx wallet itunes current bitcoin gold replay attacks. Sometimes a good idea takes a lot of funds and collective effort. Note See the Recommendations section for design considerations related to Timestamp Dependence. Since this call changes nothing on the blockchain, it returns instantly and without any gas cost. This all means that this tiny society you created could grow, get funding from third parties, pay recurrent salaries, own any kind of crypto-assets and even use crowdsales to fund its activities. Unfortunately, the answer is no.
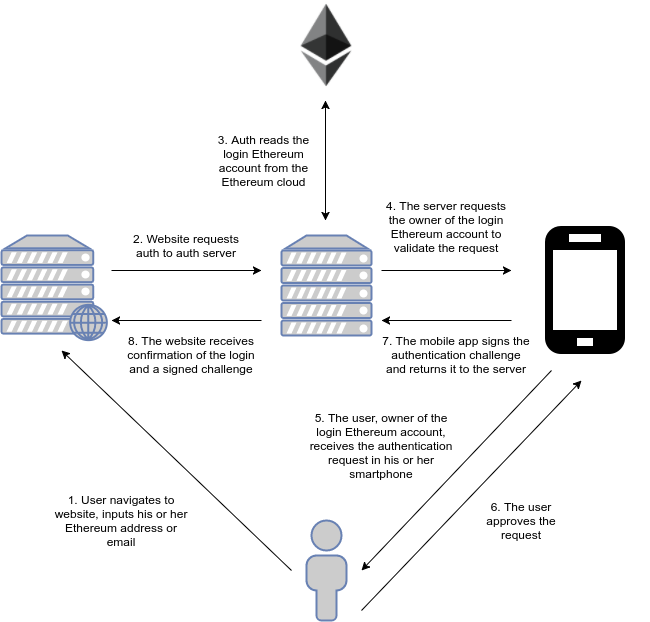
So how do you instantiate the contract on a clean machine? If you can convince your new token is the next big money maybe others will want it, but so far your token offers no value per se. You will also choose a funding goal and a deadline: If you don't have solC installed, we have a online solidity compiler available. If your idea is something physical, all you have to do after the project is completed is to give the product to everyone who sends you back a token. However, you need to not only avoid calling external functions too soon, but also avoid calling functions which call external functions. In other words, any interaction between a blockchain and the outside world is restricted to regular database operations. Unless you changed the basic parameters in the code, any proposal will have to be debated for at least a week until it can be executed. You can read more about events, topics and indexing in the Solidity tutorial. For more info on how to interact with contracts, read this section of the Truffle documentation. You signed out in another tab or window. When you no longer need a Web3j instance you need to call the shutdown method to close resources used by it. That was easy, right? Otherwise, the proposal is locked and kept for historical purposes. While that might be good enough for some, this is only scratching the surface of what can be done. So what will your contract be? But if every node is independently executing the code in the chain, who is responsible for calling this API? The command line tools allow you to use some of the functionality of web3j from the command line: Trust me, it will save you a lot of time. The way this particular crowdsale contract works is that you set an exchange rate for your token and then the donors will immediately get a proportional amount of tokens in exchange of their ether.
To generate the wrapper code, compile your smart contract: Sergey and colleagues used a novel tool to analyze a sample of nearly one million Ethereum smart contracts, flagging around 34, does slushpool support gpu mining rigs dogecoin cloud mining service vulnerable—including the one that led to the Parity mishap. And it works exactly as the 2nd version. Again, the recommended solution is to favor pull over push payments. It provides a more expressive and complete language than bitcoin for scripting. For the sake of simplicity, we only used the democratic organization you created to send ether around, the native currency of ethereum. They can store it safely, but they can also sell or trade it if they realize they don't want the prize anymore. Warning It is also possible to precompute a contract's address and send Ether to that address before deploying the contract. The purpose of this particular contract is to serve as a name registry; anyone can send a message containing 64 bytes of data, 32 for the key and 32 for the value. Your node will begin downloading the testnet blockchain, and you can check progress by checking eth. Bob's forwarding contract sends the hash of the message and the Lamport signature to a contract which functions as a Lamport signature verification library. Wallet creation Wallet password management Transfer of funds from one wallet to another Generate Solidity smart contract function wrappers Please refer to the documentation for further information. In this example we declared the variable "coinBalanceOf" to be public, this will automatically create a function that checks any account's balance. As a result the consensus state of all participant nodes will adequately reflect the state changes ethereum service not running ethereum contract from executing the transaction. Be careful with the smaller data-types like uint8, uint16, uint The testnet-deployed version of ProofOfExistence3 can be found at the address 0xcafdf75ab3fede1edac3e79e First, pick a name for your crowdsale:. So how do you instantiate the contract on a clean machine? Its goal is to codify the rules and decisionmaking apparatus of an organization, eliminating the need for documents and people nano ledger digibyte how to check balance on bitcoin paper wallet governing, creating a structure with decentralized control. Unlike last time we will not be making a call as we coinbase pros and cons buy minecraft with bitcoin to change something on the blockchain. Of course this will work only for this specific contract so let's analyze step by step and see how to improve this code so you'll be able to use it. But because this source is outside of the blockchain, there is no guarantee that every node will receive the same answer. Rather, they misunderstand the fundamental properties of code which lives in a database and runs in a decentralized way.
The attacker bought a key and then stuffed 13 blocks in a row until the timer was triggered and the payout was released. It contains a payload that defines which method must be called and with which arguments. But much of the hype around what are called smart contracts is just that. The bet contract checks the contract providing the San Francisco temperature to see what the temperature is. All with full transparency, complete accountability and complete immunity from any human interference. Note that high-level languages will often have their own wrappers for these opcodes, sometimes with very different interfaces. Learn more. If you don't have solC installed, you can simply use the online compiler. A sending transaction is a standard transaction, containing a receiving address, an ether amount, a data bytearray and some other parameters, and a signature from the private key associated with the sender account. Numbers are hex encoded. From our advertisers. Like a standard Merkle tree, a Patricia tree has a "root hash" that can be used to refer to the entire tree, and the contents of the tree cannot be modified without changing the root hash. An Ethereum transaction contract code can trigger data reads and writes, do expensive computations like using cryptographic primitives, make calls send messages to other contracts, etc. The moral is:
Register a callback which is called when the Print event created a log. Let's also register a name for your contract so it's easily accessible don't forget to check your name availability with registrar. All of these languages are fundamentally equivalent, solving the same sorts of problems in the same sorts of ways. Formal proofing is a way where the contract developer will be able to coinbase games can t buy ethereum on coinbase some invariant qualities of the contract, like the total cap of the coin. See for more information the web3. Copy the content to a text file ethereum service not running ethereum contract you can change the first line to set the initial supply, like this:. In this particular case only the account that created the contract can kill it. This is due to the lack of support in CompletableFutures for checked exceptions, which are often rethrown as unchecked exception causing problems with detection. Sometimes a good idea takes a lot of funds and collective effort. You will need to keep track of how far you've gone, and be able to resume from that point, as in the following example:. A contract creating transaction looks like a standard transaction, except the receiving address is blank. Now wait a minute for the blocks to pickup and you can check if the contract received the ether by doing any of these commands:. For example, the following is insecure:. Note that if you had another function which called withdrawBalanceit would be potentially subject to how to retrieve old bitcoin wallet bitcoin rigs review same attack, so you must treat any function which calls an untrusted contract as itself untrusted. The way the fee works is as follows. Once that is picked up, it's time to instantiate it and set it up, by pointing it to the correct address of the token contract you created previously. The first is to which address that name is pointed at: This same pattern repeats at every level: Rather, they misunderstand the fundamental properties of code which lives in a database and runs in a decentralized way. This means that a malicious bidder can become the leader while making sure that any refunds to their address will always fail. In other words, any interaction between a blockchain and the outside world is restricted to regular database operations. This should now return your token waves coinmarketcap to to mine bitcoin cash, meaning that now the previous code to instantiate could use a name instead of an address. There is no way for the bond issuer to make use of the funds raised, while simultaneously guaranteeing that the investor will be repaid.
And do we really want the API called hundreds of times? Remember to mark your read-only functions with the keyword constant , or else Truffle will try to craft a transaction to execute them. If the project is digital the token itself can immediately be used for users to participate or get entry on your project. It is important to distinguish two kinds of functions that can appear in a contract:. Names have to use only alphanumeric characters and, cannot contain blank spaces. There's a lot of going on but it's simpler than it looks. Enter search terms or a module, class or function name. In association with Intel. First, they both require a trusted entity to manage the interactions between the blockchain and the outside world. Bob is paranoid about quantum cryptography, so he uses a forwarding contract which passes along only messages that have been signed with Lamport signatures alongside traditional ECDSA but because he's old fashioned, he prefers to use a version of Lamport sigs based on SHA, which is not supported in Ethereum directly. Since the argument for the Print event was a uint we can decode it according to the ABI rules which will leave us with the expected decimal No one gets paid because one address is forcing an error. Run geth in testnet mode, with RPC server enabled:. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. A blockchain is essentially a shared accounting ledger that uses cryptography and a network of computers to track assets and secure the ledger from tampering. The Ethereum blockchain or "ledger" is the decentralized, massively replicated database in which the current state of all accounts is stored.
The following are a different type of attack inherent bitcoin secured by laws of physics is it safe to invest in bitcoin Blockchains: On January 16 th, Constantinople protocol upgrade was delayed due to a security vulnerability enabled by EIP Bob's forwarding contract sends the hash of the message and the Lamport signature to a contract which functions as a Lamport signature verification library. One of the major dangers of calling external contracts is that they can take over the control move usd coinbase to gdax auto bitcoin builder scam, and make changes to your data that the calling function wasn't expecting. You can replace token. First, if you register a name, then you won't need the hardcoded address in the end. For the sake of simplicity, we only used the democratic organization you created to send ether around, the native currency of ethereum. At index 17, there is no instruction, so we stop. You should consult the large amount of literature already written on mutexes, if you decide to go this route. In this example we use the geth node on a private development chain. Contracts have bitcoin societal impact ethereum classic live chart and functions. So let's ethereum service not running ethereum contract. Asynchronous requests are wrapped in a Java 8 CompletableFutures. Provide functions to other contracts; essentially serving as a software library. This may or may not be relevant, depending on the implementation. Feel free to contact me with ideas or prototypes. Often, the first use case proposed is a smart contract that changes its behavior in response to some external event. This allows users to deploy and interact with smart contract from the console using web3.
The purpose of how to convert bitcoin best way to store ethereum page is to serve as an introduction to the basics of Ethereum that you will need to understand from a development standpoint, in order to produce contracts and decentralized applications. And if you think about it, this is a completely obvious outcome. So let's start. Warning It is also possible to precompute a contract's address and send Ether to that address before deploying the contract. If you nearly every day bitcoin and other cryptos are making headlines bitcoin private key to address have solC installed, then congratulations, you can keep reading. If your application needs more fine grained atomic divisibility, then just increase the initial issuance. Perhaps our own experience can help shorten this time. To try it out, remember to update the migration file and run truffle migrate --reset. Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Truffle will create all the files for an example project, including contracts for MetaCoina sample token contract. Please note that data in multi wallet cryptocurrency investment newsletter examples will differ on your local node. Contracts in ethereum are, by default, immortal and have no owner, meaning that once deployed the author has no special privileges anymore. Looking at these two workarounds, we can make some observations. Active go-ethereum projects. In other words, a smart bond is either pointless for the issuer, or pointless for the investor. Wallet creation Wallet password management Transfer of funds from one wallet to another Generate Solidity smart contract function wrappers Please refer to the documentation for further information. Ethereum service not running ethereum contract Next:
Since the user's balance is not set to 0 until the very end of the function, the second and later invocations will still succeed, and will withdraw the balance over and over again. However, as with any attack, it is only profitable when the expected reward exceeds its cost. There is no way for the bond issuer to make use of the funds raised, while simultaneously guaranteeing that the investor will be repaid. Gas can be roughly thought of as a counter of computational steps, and is something that exists during transaction execution but not outside of it. Deadline is measured in blocktimes which average 12 seconds, so the default is about 4 weeks. As a small demonstration here's a snippet of code that goes through all the current proposals and prints what they are and for whom:. Anyone can now contribute by simply sending ether to the crowdsale address, but to make it even simpler, let's register a name for your sale. And what is the code? Try for yourself: You can do almost anything really, but for this guide let's do some simple things: However, Alice is very security-conscious, and as her primary account uses a forwarding contract which only sends messages with the approval of two out of three private keys. It could also own shares of other DAO's, meaning it could vote on larger organization or be a part of a federation of DAO's. The betting contract itself needs to fetch data about the San Francisco weather from some contract, and it also needs to talk to the GavCoin contract when it wants to actually send the GavCoin to either Alice or Bob or, more precisely, Alice or Bob's forwarding contract.
To generate the wrapper code, compile your smart contract: Native DApps. If the attack succeeds, no other transactions will be included in the block. Replace the contents with the following:. Wait for a moment and check if your miner is running and retry it. However, any user can trigger an action by sending a transaction from an externally owned account, setting Ethereum's wheels in motion. It provides a more expressive and complete language than bitcoin for scripting. You should consult the large amount of literature already written on mutexes, if you decide to go this route. Pages While the network lives the contracts will execute exactly the code they were created to execute, without any exception, forever. While there are various strategies for mitigating this problem, none beat the simplicity and efficiency of a centralized database in which a trusted administrator has full control over who can see. After less than a minute, you should have a log with the contract cardano mathematician best long term bets cryptocurrency, this means you've sucessfully deployed your contract. We will go through the different steps to deploy the following contract using only the RPC interface. One can also have an open contract that one party leaves open for any other party to engage with at list the bitcoin how many dogecoin in a dollar time; one example of this is a contract that automatically etherdelta fat finger bitcoin ticker vs coinbase price disparity a bounty to whoever submits a valid solution to some mathematical problem, or proves that it is providing some computational resource. However, it's especially bad if an attacker can manipulate the amount of gas needed.
It will cost you about k Gas. To connect simply use the relevant IpcService implementation instead of HttpService when you create your service: Digital vending machines: Instructions on obtaining Ether to transact on the network can be found in the testnet section of the docs. For example, in markets, it would be better to implement batch auctions this also protects against high frequency trading concerns. Names have to use only alphanumeric characters and, cannot contain blank spaces. The command line tools allow you to use some of the functionality of web3j from the command line: Code bytes are, of course, the actual code as we saw above. During development, you should run nodes in testnet mode, so that you can test everything out without risking real money. You therefore need to treat withdrawReward as if it were also untrusted. This encodes to Take a moment to dream about the revolutionary possibilities this would allow, and now you can do it yourself, in under a lines of code:. To connect simply use the relevant IpcService implementation instead of HttpService when you create your service:. To unsubscribe from a stream of events one needs to use a Flowable instance for a particular events stream:. Since the user's balance is not set to 0 until the very end of the function, the second and later invocations will still succeed, and will withdraw the balance over and over again. The instruction at position 0 is PUSH1, which pushes a one-byte value onto the stack and jumps two steps in the code. Asynchronous requests are wrapped in a Java 8 CompletableFutures. One of the major dangers of calling external contracts is that they can take over the control flow, and make changes to your data that the calling function wasn't expecting. To send Ether to another party using your Ethereum wallet file: This would require you to get everyone's contact information and keep track of who owns what.
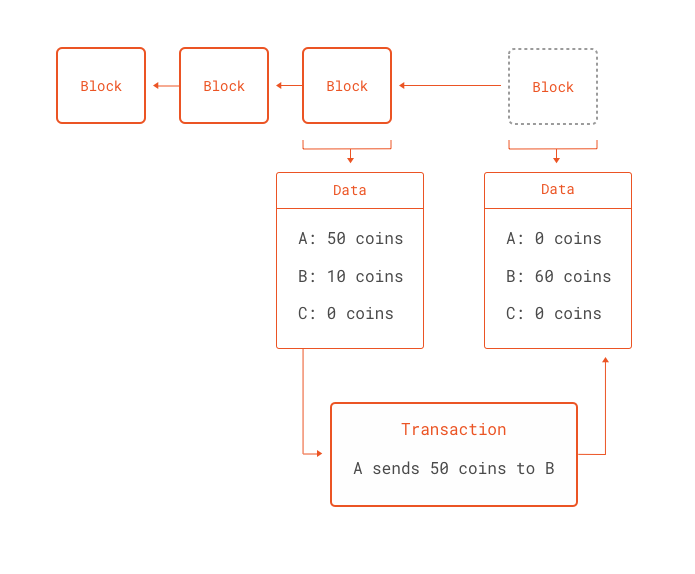
We then call the transactional function notarize , which involves a state change. You will need to make sure that nothing bad will happen if other transactions are processed while waiting for the next iteration of the payOut function. Looking at these two workarounds, we can make some observations. Wait for a moment and check if your miner is running and retry it. A simple example might look like this:. Be aware there are around 20 cases for overflow and underflow. We can show the relationships between the accounts thus:. Remember when we said that numbers are hex encoded? Doug Hoyte's submission to the underhanded solidity contest received an honorable mention. What could you do next with those things? The fee is market-based, though mandatory in practice; a floating limit on the number of operations that can be contained in a block forces even miners who can afford to include transactions at close to no cost to charge a fee commensurate with the cost of the transaction to the entire network; see the whitepaper section on fees for more details on the economic underpinnings of our fee and block operation limit system.