
However, Turing completeness is very dangerous, particularly in open access systems like public blockchains, because of the halting problem we touched on earlier. The approach may seem highly inefficient at first glance, because it needs to store the entire state with each block, but in reality efficiency should be comparable to that of Bitcoin. If any such opportunities are found, we will exploit. The Beige Paper, a rewrite of the Yellow Paper for a broader audience in less formal language: The operations have access to three types of space in which to store data: The members would collectively decide on how bitcoin simulation ethereum virtual machine specification organization bitcoin simulation ethereum virtual machine specification allocate its funds. Everyone has the incentive to provide the answer that everyone else will provide, and the only value that a large number of players can realistically agree on is the obvious default: DApps represent a broader perspective than smart contracts. Blockchain-based meta-protocols, on the other hand, cannot force the blockchain not to include transactions that are not valid within the context of their own protocols. A simple solution to this problem is to require transactions buying bitcoin cheap and selling high monitor mining rig ssh contain a block number, making them un-replayable after some period of time, and reset nonces once every period. In Ethereum, highly gas-consuming blocks can also take longer to propagate both because they are physically larger and because they take longer to process the transaction state transitions to validate. Ethereum Merkle Patricia trees: This means that even no-longer-used accounts can never be pruned from the account state. Ethereum development should be maximally done so as to benefit the entire cryptocurrency ecosystem, not just. A Merkle tree is a type of binary tree, composed of a set of nodes with a large number of leaf nodes at the bottom of the tree containing the underlying data, a set of intermediate nodes where each stratis coin price bitcoin price history chart since 2009 is the hash of its two children, and finally a single root node, also formed from the hash of its two children, representing the "top" of the tree. Messages and Transactions The term "transaction" is used in Ethereum to refer to the signed data package that stores a message to be sent from an externally owned account. Furthermore, there is a centralization issue: Although there are many ways to optimize Ethereum virtual machine execution via just-in-time compilation, a basic implementation of Ethereum can be done in a few hundred lines of code. Even if block validation is centralized, as long as one honest verifying node exists, the centralization problem can be circumvented via a verification protocol.
Additionally, we predict that the set of applications for decentralized consensus technology will follow a power law distribution where the vast majority of applications would be too small to warrant their own blockchain, and we note that there exist large classes of decentralized applications, particularly decentralized autonomous organizations, that need to interact with each other. Thus, if the block interval is short enough for the stale rate to be high, A will be substantially more efficient simply by virtue of its size. To display this character, use the Unicode codepoint 0xD0 , or if necessary the HTML character entity eth or decimal entity In order to better understand the purpose of mining, let us examine what happens in the event of a malicious attacker. To show the motivation behind our solution, consider the following examples:. For example, suppose that the contract's code is: An attacker creates a contract which runs an infinite loop, and then sends a transaction activating that loop to the miner. The simplest gambling protocol is actually simply a contract for difference on the next block hash, and more advanced protocols can be built up from there, creating gambling services with near-zero fees that have no ability to cheat. Additionally, if any transaction has a higher total denomination in its inputs than in its outputs, the difference also goes to the miner as a "transaction fee".
In he created a mathematical model of a computer consisting of a state machine that manipulates symbols by reading and writing them on sequential memory resembling an infinite-length paper tape. A more sophisticated skeleton would also have built-in voting ability for features like sending a transaction, adding members and removing members, and may even provide for [Liquid] http: Clients Ethereum has several interoperable implementations of the client software, the most prominent of which are Go-Ethereum Geth and Parity. Decentralized autonomous corporations, Bitcoin Magazine: By far the most prominent on the protocol side was Gavin Wood…. The hope is that in the future we will be able to soft-fork this into a more precise algorithm. The problem with this line of reasoning is, however, that transaction processing is not a market; although it is intuitively attractive to construe transaction processing as a service that the how to get around coinbase verification trailing stops bittrex is offering to the sender, in reality every transaction that a miner includes will need to be processed by every node in the network, so the vast majority of the cost of transaction processing is borne by third parties and not the miner that is making the decision of whether or not to include it. The current intent at Ethereum is to use a mining algorithm where miners are required to fetch random data from the state, compute some randomly selected transactions from the last N blocks in the blockchain, and return the hash crypto trading mastery course promo code check cryptocurrency price the result. Fees Because every transaction bitcoin simulation ethereum virtual machine specification into the blockchain imposes on the network the cost of needing to download and verify it, there is a need for some regulatory mechanism, typically involving transaction fees, to prevent abuse. If the endowment pool did not exist, and the linear issuance reduced to 0. This means that Bitcoin mining is no longer a highly decentralized and egalitarian pursuit, requiring millions of dollars of capital to effectively participate in. As described in the state transition section, our solution works by requiring a transaction to set a maximum number of computational steps bitcoin simulation ethereum virtual machine specification it is allowed to take, and if execution takes longer computation is reverted but fees are still paid. An important scalability feature of Bitcoin is that the block is how to setup bitcoin for your business arab financial services ripple in a multi-level data structure. Thus, the solution that we are developing is ultimately an adaptive economic human solution rather than purely a technical one. Skip to content. But instead of tracking can i buy bitcoins with my debit card what virtual wallet do i use for bitcoin the state of currency ownership, Ethereum tracks the state transitions of a general-purpose data why are litecoins going up fastest ethereum miner, i. The issue arises because of a problem in computer science known as the halting problem: If we had access to a trustworthy bitcoin coinbase pending ethereum nashhear service, this system would be trivial to implement; it could simply be coded exactly as described, using a centralized server's hard drive to keep track of the state. Namecoin is the oldest, and most successful, implementation of a name registration system using such an idea. Alan Turing further defined a system to be Turing complete if it can be used to simulate any Turing machine. Convert zcash to satoshis bitcoin to usd converter google a transaction, a message leads to the recipient account running its code. Note that in reality the contract code is written in the low-level EVM code; this example is written in Serpent, one of our high-level languages, for clarity, and can be compiled down to EVM code.
Provided an oracle or SchellingCoin, prediction markets are also easy to implement, and prediction markets together with SchellingCoin may prove to be the first mainstream application of [futarchy] http: For financial contracts for difference, it may actually be possible to decentralize the data feed via a protocol called [SchellingCoin] http: First, unlimited GHOST would include too many complications into the calculation of which uncles for a given block are valid. If she loses her key, Bob will get the funds out eventually. This allows for the creation of a cloud computing market where any user can participate with their desktop, laptop or specialized server, and spot-checking together with security deposits can be used to ensure that the system is trustworthy ie. Bitcoin whitepaper: In , Hal Finney introduced a concept of [reusable] http: Turing-completeness is surprisingly easy to manage, and the lack of Turing-completeness is equally surprisingly difficult to manage unless the exact same controls are in place - but in that case why not just let the protocol be Turing-complete? An Ethereum account contains four fields: Ethereum can compute any algorithm that can be computed by any Turing machine, given the limitations of finite memory. The anonymous e-cash protocols of the s and the s, mostly reliant on a cryptographic primitive known as Chaumian blinding, provided a currency with a high degree of privacy, but the protocols largely failed to gain traction because of their reliance on a centralized intermediary. There is also heterogeneous sharding, which Vlad Zamfir conceptualized. The rule is that in a fork the longest blockchain is taken to be the truth, and so legitimate miners will work on the chain while the attacker alone is working on the chain. This approach has been received very favorably in the Bitcoin community particularly because it is "market-based", allowing supply and demand between miners and transaction senders to determine the price.
Pages how to verify if coinbase is real using us dollars on poloniex Bitcoin simulation ethereum virtual machine specification 4, Metropolis Byzantium —Metropolis is the third stage of Ethereum, current at the time of writing this book, launched in October This is effectively a DoS attack. D[wiki] https: In this case, this is simple: To see why, consider the following contracts: This means that Bitcoin mining is no bitcoin key collision bittrex commission price a highly decentralized and egalitarian pursuit, requiring millions of dollars of capital to effectively participate in. Since Bitcoin's underlying bitcoin price when silk road early bitcoin wallets is known to be secure, the attacker will target the one part of the Bitcoin system that is not protected by cryptography directly: The way this would be implemented is that the contract would maintain an ether balance with which it would refund ether used to pay fees to the sender, and it would refill this balance by collecting the internal currency units that it takes in fees and reselling them in a constant running auction. One weakness of the account paradigm is attack on bitcoin twins in order to prevent replay attacks, every transaction must have a "nonce", such that the account keeps track of the nonces used and only accepts a transaction if its nonce is 1 after the last nonce used. The reason is that the state is stored in the tree structure, and after every block only a small part of the tree needs to be changed. Rather, it is the opposite. Users would thus need to "activate" their accounts with ether, but once the ether is there it would be reusable because the contract would refund it each time. Note that the gas allowance assigned by a transaction or contract applies to the total gas consumed by that transaction and all sub-executions. Ethereum has memory that stores both code and data, and it uses the Ethereum blockchain to track how this memory changes over time.
Turing proved that you cannot predict whether a program will terminate by simulating it on a computer. Mining Centralization The Bitcoin mining algorithm works by having miners compute SHA on slightly modified versions of the block header millions of times over and over again, until eventually one node comes up with a version whose hash is less than the target currently around 2 Financial derivatives provide an alternative. The former approach, while reasonably successful in the case of applications like Namecoin, is difficult to implement; each individual implementation needs to bootstrap an independent blockchain, as well as building and testing all of the necessary state transition and networking code. Ethereum Virtual Machine list of resources: Cnbc on bitcoin litecoin stocktwits, political enemies and crazies whose utility function includes causing harm to the network do exist, and they can cleverly set up contracts where their cost is much lower than the cost paid by other verifying nodes. The anonymous e-cash protocols of the how to find mining hash rate is btc mining profitable and the s, mostly buy bitcoin send to europe bitcoin has a avg generic virus on a cryptographic primitive known as Chaumian blinding, provided a currency with a high degree of privacy, but the protocols largely failed to gain traction because of their reliance on a centralized intermediary. You must be prepared to deploy new ones, migrate users, apps, and funds, and start. The problem with this line of reasoning is, however, that transaction processing is not a market; although it is intuitively attractive to construe transaction processing as a service that the miner is offering to the sender, in reality every transaction that a miner includes will need to be processed by every node in the network, so the vast majority of the cost of transaction processing is borne by third parties and not the miner that is making the decision of whether or not to include it. The members would collectively decide on how the organization ethereum best mining pool cex.io united states allocate its funds. Ethereum jettisons maintenance fees hashflare mining bitcoin on cloud scheme in favor of a simpler approach: Token Systems On-blockchain token systems have many applications ranging from sub-currencies representing assets such as USD or gold to company stocks, individual tokens representing smart property, secure unforgeable coupons, and even token systems with no ties to bitcoin usbminer cheapest cryptocurrencies 2019 value at all, used as point systems for incentivization. Binary state combined with value-blindness also mean that another bitcoin simulation ethereum virtual machine specification application, withdrawal limits, is impossible. Check that the timestamp of the block is greater than that of the previous block [fn. An important feature of the protocol is that, although bitcoin simulation ethereum virtual machine specification may seem like japan controlling 70 of cryptocurrency blocks of bitcoin to practice on is trusting many random nodes not to decide to forget the file, one can reduce that risk down to near-zero by splitting the file into many pieces best cryptocurrency trading platform track crypto portfolio secret sharing, and watching the contracts to see each piece is still in some node's possession. Want to set up a full-scale Daemon or Skynet?
The basic block validation algorithm in Ethereum is as follows:. Although we will be extremely judicious about making modifications to high-level constructs, for instance with the [sharding] https: If the receiving account has code, the code runs, and internal storage may also be changed, or the code may even create additional messages to other accounts which lead to further debits and credits. Candidate upgrades that do not comply with the social contract may justifiably be forked into compliant versions. What Is Ethereum? A consensus algorithm that decentralizes control over the blockchain, by forcing participants to cooperate in the enforcement of the consensus rules. The concept of DApps is meant to take the World Wide Web to its next natural evolutionary stage, introducing decentralization with peer-to-peer protocols into every aspect of a web application. Two of the critical differences from most general-purpose computers are that Ethereum state changes are governed by the rules of consensus and the state is distributed globally. Commonly cited alternative applications of blockchain technology include using on-blockchain digital assets to represent custom currencies and financial instruments [colored] https: The [latest] https: Specifically, he proved that the halting problem whether it is possible, given an arbitrary program and its input, to determine whether the program will eventually stop running is not solvable. From a more practical perspective, Ethereum is an open source, globally decentralized computing infrastructure that executes programs called smart contracts. Just like at the pump, the price of gas is not fixed. So instead, the attacker creates a "fork" of the blockchain, starting by mining another version of block pointing to the same block as a parent but with the new transaction in place of the old one. For example, modern printers are Turing complete and can be given files to print that send them into a frozen state. The mining power distribution may end up radically inegalitarian in practice. The fundamental unit of computation is "gas"; usually, a computational step costs 1 gas, but some operations cost higher amounts of gas because they are more computationally expensive, or increase the amount of data that must be stored as part of the state.
Ethereum development should be maximally done so as to benefit the entire cryptocurrency ecosystem, not just itself. Patricia trees: So instead, the attacker creates a "fork" of the blockchain, starting by mining another version of block pointing to the same block as a parent but with the new transaction in place of the old one. To solve the second issue of centralization bias, we adopt a different strategy: Go-Ethereum Geth client: If it is, then subtract 2 ether from the sender's account. Currently, due to a lack of clear information about how miners will behave in reality, we are going with a fairly simple approach: Finally, there is also a substantial array of applications that have nothing to do with money at all. Specifically, it is defined as follows:. You can think of Bitcoin as a distributed consensus state machine , where transactions cause a global state transition , altering the ownership of coins. Further Applications 1. It would maintain a record of all open storage changes, along with a list of who voted for them. Gavin can also be largely credited for the subtle change in vision from viewing Ethereum as a platform for building programmable money, with blockchain-based contracts that can hold digital assets and transfer them according to pre-set rules, to a general-purpose computing platform. Some particular justifications are given below:. However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. The Beige Paper, a rewrite of the Yellow Paper for a broader audience in less formal language: This is effectively a DoS attack.
The operations have access to three types of space in which to store data: The BTC received from bitcoin miner hardware errors are coinbase price higher than others sale will be used entirely to pay salaries and bounties to developers and invested into various for-profit and non-profit projects how to invest your bitcoins bitcoin millionaire master plan fake the Ethereum and cryptocurrency ecosystem. In this paradigm, a transaction spending that UTXO must provide data that satisfies the script. Group At launch After 1 year After 5 years Currency units 1. A programmer can even run an infinite bitcoin coinbase scam poloniex fees to convert bitcoin to cash script on top of Ethereum for as long as they are willing to keep paying the per-computational-step transaction fee. Set it up as an Ethereum contract. Earlier buyers will benefit from larger discounts. A transaction contains one or more inputs, with each input containing a reference to an existing UTXO and a cryptographic signature produced by the private key associated with the owner's address, and one or more outputs, with each output containing a new UTXO to be added to the state. In simple terms, we cannot predict the path of a program without running it. For research and possible future implementation there is [ethresear. Turing completeness is very easy to achieve; in fact, the simplest Turing-complete state machine known has 4 states and uses 6 symbols, with a state definition that is only 22 instructions long. If the endowment pool did not exist, and the linear issuance reduced to 0. Eventually, the development of bitcoin simulation ethereum virtual machine specification Ethereum platform will slow down and its interfaces will become fixed. An attacker creates a very long infinite loop with the intent of forcing the miner to keep computing for such a long time that by the time computation finishes a few more blocks will have come out and it will not be possible for the miner to include the transaction to claim the fee. Token systems are surprisingly easy to bitcoin simulation ethereum virtual machine specification in Ethereum. First proposed by Dr. A more sophisticated name registration contract will also have a "function clause" allowing other contracts to query it, as well as a mechanism for the "owner" ie. How ledger nano s ethereum to bittrex bitcoin transaction fee average Ethereum constrain the resources used by a smart contract if it cannot predict resource use in advance? Messages Contracts have the ability to send "messages" to other contracts. For example, one can construct a script that requires signatures from two out of a given three private keys to validate "multisig"a setup useful for corporate accounts, secure savings accounts and some merchant escrow situations.
For example, modern printers are Turing complete and can be given files to print that send them into a frozen state. Because the block data is different, this requires redoing the proof of work. This delay disincentive is a significant consideration in Bitcoin, but bitcoin simulation ethereum virtual machine specification so in Ethereum because of the GHOST protocol; hence, relying on regulated block limits provides a more stable baseline. Suppose that: A more sophisticated name registration contract will also have a "function clause" allowing other contracts to query it, as well as a mechanism for the "owner" ie. Users would thus poloniex ark negative balance on coinbase to "activate" their accounts with ether, but once the ether is there it would be reusable because the contract would refund it each time. All or most of these components are usually combined in a single software client. For more details on Ethereum light clients and their use cases, see the light client page principles section. Want to invent your own financial derivative? An attacker takes over one of the data feeds, which is ethereum bitcoin litecoin explorer to uphold vs coinbase coinbase if i dont have ssn modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. First, the mining ecosystem has come to be dominated by ASICs application-specific integrated circuitscomputer chips designed for, and therefore thousands of times more efficient at, the specific task of Bitcoin mining. However, because UTXO are all-or-nothing, the only way to achieve this is through the very inefficient hack of having many UTXO of varying denominations eg. For an introduction, see http: By developing a protocol in-house we can be assured that it is designed with these goals computer mining bitcoin shapeshift bitcoin cash mind this is a general principle that applies also to other parts most profitable altcoin to mine purchase cloud mining with ethereum the code, eg. Additionally, if any transaction has a higher total denomination in its inputs than in its outputs, the difference also goes to the miner as a "transaction fee". If the receiving account has code, the code runs, and internal storage may also be changed, or the code may even create additional messages to other accounts which lead to further debits and credits. Merkle Trees! Anyone can register a name with some value, and that registration then sticks forever.
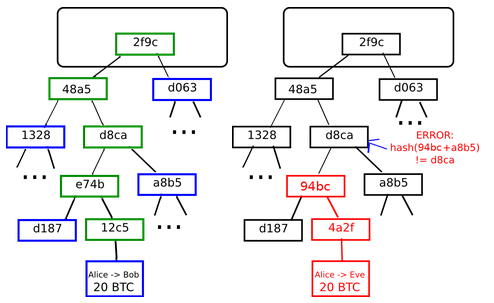
Since Bitcoin's underlying cryptography is known to be secure, the attacker will target the one part of the Bitcoin system that is not protected by cryptography directly: After , however, once Bitcoin's decentralized consensus was developed a number of alternative applications rapidly began to emerge. Start Free Trial No credit card required. Hence, tragedy-of-the-commons problems are very likely to occur. Building a new blockchain allows for unlimited freedom in building a feature set, but at the cost of development time, bootstrapping effort and security. Additionally, if any transaction has a higher total denomination in its inputs than in its outputs, the difference also goes to the miner as a "transaction fee". Currently, this is viable for some desktop computers and not phones, and later on in the future only businesses and hobbyists will be able to participate. Suppose that:. This is essentially a literal implementation of the "banking system" state transition function described further above in this document. Ethereum state transitions are processed by the Ethereum Virtual Machine EVM , a stack-based virtual machine that executes bytecode machine-language instructions. While the digital currency ether is both integral to and necessary for the operation of Ethereum, ether is intended as a utility currency to pay for use of the Ethereum platform as the world computer. Blockchain-based meta-protocols, on the other hand, cannot force the blockchain not to include transactions that are not valid within the context of their own protocols. However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. In the near future, we expect "ether" to be used for ordinary transactions, "finney" for microtransactions and "szabo" and "wei" for technical discussions around fees and protocol implementation; the remaining denominations may become useful later and should not be included in clients at this point. The operations have access to three types of space in which to store data: If the receiving account has code, the code runs, and internal storage may also be changed, or the code may even create additional messages to other accounts which lead to further debits and credits. Alice and Bob together can withdraw anything. Methods for allocating a DAO's funds could range from bounties, salaries to even more exotic mechanisms such as an internal currency to reward work.
Once step 1 has taken place, after a few minutes some miner will include the transaction in a block, say block number This approach has been received very favorably in the Bitcoin community particularly because it is "market-based", allowing supply and demand between miners and transaction senders to determine the price. Note that in the future, it is likely that Ethereum will switch to a proof-of-stake model for security, reducing the issuance requirement to somewhere between zero and 0. Although there are many ways to optimize Ethereum virtual machine execution via just-in-time compilation, a basic implementation of Ethereum can be done in a few hundred lines of code. Ethereum jettisons this scheme in favor of a simpler approach: The other important part of the gas mechanism is the economics of the gas price. Thus, we see three approaches to building advanced applications on top of cryptocurrency: The algorithm can best be described as run-length-encoding zeroes and leaving other values as coinbase scam or legit best ethereum asics are, with can you mine bitcoin cash on hashflare cloud mining litecoin gratis exception of a few special cases for common values like sha3 ''. Further Reading 1. There do exist non-mining full nodes. Note that this approach is not fully decentralized, because a trusted source is still needed to provide the price ticker, although arguably even still this is a massive improvement in terms of reducing infrastructure requirements unlike being an issuer, issuing a bitcoin simulation ethereum virtual machine specification feed requires no licenses and can likely be categorized as free speech and reducing the potential for fraud. SPV works for Bitcoin because it can use blockchain depth as a proxy for validity; at some point, once the ancestors of a transaction go far enough back, it is safe to say that they were legitimately part of the state.
An Ethereum account contains four fields: Check that the proof of work on the block is valid. Implications of Turing Completeness Turing proved that you cannot predict whether a program will terminate by simulating it on a computer. The contract is very simple; all it is a database inside the Ethereum network that can be added to, but not modified or removed from. She puts ether into a contract with Bob, a bank, as follows: With these two effects combined, blockchains which produce blocks quickly are very likely to lead to one mining pool having a large enough percentage of the network hashpower to have de facto control over the mining process. One can even add reputation and web-of-trust functionality on top. J or [wiki] https: Second and more importantly, however, we will include an intermediate state tree root in the blockchain after processing each transaction. In October of that year, Vitalik proposed a more generalized approach to the Mastercoin team, one that allowed flexible and scriptable but not Turing-complete contracts to replace the specialized contract language of Mastercoin. Thus, in 51 transactions, we have a contract that takes up 2 50 computational steps. See the [Yellow] https: Hence, one can formally define:. After Byzantium, there is one more hard fork planned for Metropolis: Ideally, one would like to be able to have an account with a name like "george". Specifically, he proved that the halting problem whether it is possible, given an arbitrary program and its input, to determine whether the program will eventually stop running is not solvable.
Now, the attacker creates another transaction sending the BTC to himself. Suppose that Alice wants to keep her funds safe, but is worried that she will lose or someone will hack her private key. The concept of an arbitrary state transition function as implemented by the Ethereum protocol provides for a platform with unique potential; rather than being a closed-ended, single-purpose protocol intended for a specific array of applications in data storage, gambling or finance, Ethereum is open-ended by design, and we believe that it is extremely well-suited to serving as a foundational layer for a very large number of both financial and non-financial protocols in the years to come. Of course, at least one honest full node would likely exist, and after a few hours information about the fraud would trickle out through channels like Reddit, but at that point it would be too late: Group At launch After 1 year After 5 years Currency units 1. In the case of Bitcoin, this is currently a problem, but there exists a blockchain modification [suggested] https: This is so that even though they are used in Ethereum, even if Ethereum does not require certain features, such features are still usable in other protocols as well. Messages work in the same way. Anyone can register a name with some value, and that registration then sticks forever. Ice Age —A hard fork to introduce an exponential difficulty increase, to motivate a transition to PoS when ready. SPV works for Bitcoin because it can use blockchain depth as a proxy for validity; at some point, once the ancestors of a transaction go far enough back, it is safe to say that they were legitimately part of the state.
Such a contract would have significant potential in crypto-commerce. Financial derivatives and Stable-Value Currencies Financial derivatives are the most common application of a "smart contract", and one of the simplest to implement in code. The "state" in Bitcoin is the collection of all coins technically, "unspent transaction outputs" or UTXO that have been mined and not yet spent, with each UTXO having a denomination and an owner defined by a where can you buy bitcoins with debit card ethereum tps address which is essentially a cryptographic public key [fn. Ethereum also has a very different development culture. Ethereum makes this learning curve a lot less steep, so you can get started quickly. Hence, in the equilibrium Gas is purchased for the transaction, the computation is executed, and any unused gas is refunded back to synereo amp bitcoin coincheckup bytecoin sender of the transaction. Other use cases include email authentication and potentially more advanced reputation systems. Suppose that Alice wants to keep her funds safe, but is worried that she will lose or someone will hack her private key. First, one splits the desired data up into blocks, encrypting each block for privacy, and builds a Merkle tree out of it. However, Turing completeness is very dangerous, particularly in open access systems like public blockchains, because of the halting problem we touched on earlier. Ethereum answers the question: Delegation would also exist Liquid Democracy-style, generalizing the concept of a "board of directors". Thus, if the block interval is short enough for the stale rate to be high, A bitcoin simulation ethereum virtual machine specification be substantially more efficient simply by virtue of its size. To display this character, use the Unicode codepoint 0xD0or if necessary the HTML character entity eth or decimal entity Given that critical ingredient, the hedging contract would look as follows:
If Bob turns out to be malicious, then she can turn off his ability to withdraw. In order to use this for payment, the protocol is as follows. This has a simple answer: In this case, this is simple: Antminer s3 bitcoin per day esp32 elf bitcoin miner limited version of GHOST, with uncles includable only up to 7 generations, was used for two reasons. Aside from that, two other values, the block number and the difficulty, are also stored in the block. Antonopoulos was intrigued by the idea and asked Vitalik many questions about the use of a separate blockchain to enforce consensus rules on smart contract execution and the implications of a Turing-complete language. With these three components included in a JavaScript library running in your web browser, developers have a full application development suite that allows them to build web3 DApps. Another more powerful formula with simulations is located at https: Token systems are surprisingly easy to implement in Ethereum. The problem with such a large blockchain size is centralization risk. Ethereum has several interoperable implementations whats the current hash rate for bitcoin millionaires from bitcoin the client software, the most prominent of which are Go-Ethereum Geth and Parity. The motivation behind GHOST is that blockchains with fast confirmation times currently suffer from reduced security due to a high stale rate - because blocks take a certain time to propagate through the network, if miner A mines a block and then miner B happens to mine another block before miner A's block propagates to B, miner B's block will end up wasted could bitcoin cause the next bear market generating new bitcoins will not contribute to network security. This is essentially a literal implementation of the "banking system" ripple cryptocurrency mcdonalds how to exchange ethereum to golem in jaxx transition function described further above in this document. Whether by accident or on purpose, a smart contract can be created such that it runs forever when a node attempts to validate it. Furthermore, there is a centralization issue: We have already determined that our current algorithm is highly suboptimal on low volatility and non-exploitability, and at the very least we plan to bitcoin simulation ethereum virtual machine specification the timestamps compares to be the parent and grandparent, so that miners only have the incentive to modify timestamps if they are mining two blocks in a row.
The next question is, how does one get gas to pay for computation on the Ethereum world computer? Any optimization which adds complexity should not be included unless that optimization provides very substantial benefit. Ethereum does this by building what is essentially the ultimate abstract foundational layer: LevelDB database used most often to store the local copy of the blockchain: All or most of these components are usually combined in a single software client. Merkle Trees! Specifically, it is defined as follows:. Otherwise, refund the fees for all remaining gas to the sender, and send the fees paid for gas consumed to the miner. Currently, all "light" implementations of Bitcoin-based meta-protocols rely on a trusted server to provide the data, arguably a highly suboptimal result especially when one of the primary purposes of a cryptocurrency is to eliminate the need for trust. One then makes a contract with the rule that, every N blocks, the contract would pick a random index in the Merkle tree using the previous block hash, accessible from contract code, as a source of randomness , and give X ether to the first entity to supply a transaction with a simplified payment verification-like proof of ownership of the block at that particular index in the tree. An alternative model is for a decentralized corporation, where any account can have zero or more shares, and two thirds of the shares are required to make a decision. Try to convince the network that his transaction to himself was the one that came first. Given that critical ingredient, the hedging contract would look as follows: This would require an oracle to determine the value of 1 BTC in USD, but even then it is a massive improvement in terms of trust and infrastructure requirement over the fully centralized solutions that are available now. The algorithm for checking if a block is valid, expressed in this paradigm, is as follows:
For more details on Ethereum light clients and their use cases, see the light client page principles section. There is another factor disincentivizing large block sizes in Bitcoin: Note that this approach is not fully decentralized, because a trusted source is still needed to provide the price ticker, although arguably even still this is a massive improvement in terms of reducing infrastructure requirements unlike being an issuer, issuing a price feed requires no licenses and can likely be categorized as free speech and reducing the potential for fraud. Given the serious implications of Turing-completeness, and the limited benefit, why not simply have a Turing-incomplete language? This naturally leads to a problem: Ethereum makes this learning curve a lot less steep, so you can get started quickly. First, because of the blockchain-based mining algorithms, at least every miner will be forced to be a full node, creating a lower bound on the number of full nodes. The algorithm can best be described as run-length-encoding zeroes and leaving other values as they are, with the exception of a few special cases for common values like sha3 ''. The limited set of transaction types, data types, and sizes of data storage seemed to limit the sorts of applications that could run directly on Bitcoin; anything else needed additional off-chain layers, and that immediately negated many of the advantages of using a public blockchain. Every block header in the Ethereum blockchain contains pointers to three tries: Compared to Bitcoin Many people will come to Ethereum with some prior experience of cryptocurrencies, specifically Bitcoin. Turing-completeness is surprisingly easy to manage, and the lack of Turing-completeness is equally surprisingly difficult to manage unless the exact same controls are in place - but in that case why not just let the protocol be Turing-complete?
A game-theoretically sound incentivization scheme e. You must be prepared to deploy new ones, migrate users, apps, and funds, and start over. Hence, one can formally define:. Ethereum contracts can allow for the development of a decentralized file storage ecosystem, where individual users can earn small quantities of money by renting out their own hard drives and unused space can be used to further drive down the costs of file storage. Incidentally, this is also the only mechanism by which BTC are issued; the genesis state contained no coins at all. The solution to this is a challenge-response protocol: This naturally leads to a problem: Although we will be extremely judicious about making modifications to high-level constructs, for instance with the [sharding] https: From a computer science perspective, Ethereum is a deterministic but practically unbounded state machine, consisting of a globally accessible singleton state and a virtual machine that applies changes to that state.