I'd like to donate, but currently don't have an accessible Bitcoin wallet with enough balance. In March this year, U. The public key hash is the Bitcoin address you see published. Buy Bitcoin Worldwide is not offering, promoting, or encouraging the purchase, sale, or trade of any security or coinbase processing bank account are bitcoins fixed. These private keys act as the proof of ownership for our Bitcoins. It will run and say "8 tests passed" but I'm hoping ym small donation can clarify how to implement the github code you've provided Thanks you so much for such an informative blog post, Ken! You can buy GPUs from two main vendors: Note that arrows are references to the previous outputs, so are backwards to the flow of bitcoins. We only list wallets that have published and open-sourced their code. If you get one byte wrong, the transaction is rejected with no clue as to where the problem is. Very nice. Why would I want to? Run the file that downloads and install the wallet. You can buy bitcoin on an exchange using fiat and transfer it to your hardware wallet. Unlike most regular currencies, make coinbase transaction go faster where to buy bitcoin private purchasing power declines over time, bitcoin was designed to be deflationary: As you can see by this listaverage password complexity still leaves a lot to be desired.
Note that you cannot determine the public key or the private key from the address. I would like to ripple transaction hash lookup coinbase profit calculator how to run this python code. Electrum Electrum wallet is an easy to use desktop wallet for Mac, Windows and Linux. The Ledger gives perfect deposit bitcoin review how to send bitcoin from coinbase to localbitcoin user the freedom to create their. Using a desktop wallet allows for greater security than a web wallet, and a number of different features. I mean, I guess, my address? Come tax season, your bitcoin earnings will be subject to taxation. Energy consumption All this computing power chews up electricity, and that costs money. No doubt, this has the potential to save many investors headaches in the future. The Elliptic Curve Digital Signature Algorithm ECDSA takes a message hash, and then does some straightforward elliptic curve arithmetic using the message, the private key, and a random number [18] to generate a new point on the curve that gives a signature. It is preferable because a hacker would need to have the device in their physical possession in order to access your account. The three most popular hardware wallets: Private keys emerged as a way to communicate securely through insecure communication channels. Buy Learn More. In fact, according to a review of Fox News transcripts, he has only gotten more defiant since he was reportedly scolded by executives. How do I generate a Bitcoin address for my wallet? Like a bank account last 24 hours bitcoin value ripple to bitcoin calculator, where the difference lies in the wallets having multiple addresses. The script in the old transaction is called scriptPubKey and the script in the new transaction is called scriptSig. Electrum is a good option for both beginners and advanced users. The output amount is 0.
Normal people use software [1] that hides what is really going on, but I wanted to get a hands-on understanding of the Bitcoin protocol. If you find this report helpful, please let us know. Additionally, if aesthetics matter to you, the Ledger sports an arguably sleeker design than the Trezor. With Bitcoin you have the privilege - but also the responsibility - to safeguard your own money. Where can I get the libraries? The Mt. This article with all the codes clears all of my doubts. Clean Hardware This brings us to the general best practices portion of this guide. The Gathering Online Exchange" and later took the acronym as its name. In March this year, U. Each of those inputs references a previous input, and so on. Signing the transaction is the hard part, as you'll see next. The peer-to-peer network There is no centralized Bitcoin server. What makes elliptic curves useful cryptographically is that it's fast to do integer multiplication, but division basically requires brute force. Python version 2. The next step is to send it into the peer-to-peer network, where it will be picked up by miners and incorporated into a block. Antana , CC: If you would like to receive future versions, please leave us your email to get notified of future editions.

Subscribe Here! Keep your coins in an environment where buy bitcoin atm nyc bitcoin on wix have complete control. I'm a graduate student and trying to build an application with blockchain. This brings us to the general best practices portion of this guide. Always remember to: We typically recommend setting up two-factor authentication 2FA for any and every account that offers it, even if the service is not crypto related. Structure of the example Bitcoin transaction. No, but then again, neither is the dollar. Litecoinfor example, uses a different proof of work algorithm to bitcoin, called Scrypt. Do you know of any resource that could help me in regard to coding up this SigningKey algorithm? Electrum is a good option for both beginners and advanced users. Because you think a bitcoin is worth. Most hardware wallets add some special kind of tape on the packaging to try to make any tampering more noticeable. Is bitcoin … real?
More effort may be required to build a predictive model from this data. Post a Comment. Bitwise is the most well-known of a swath of index funds that have popped up in the last 12 months. The nodes on the network exchange transactions, blocks, and addresses of other peers with each other. How Bitcoin transactions are signed The following diagram gives a simplified view of how transactions are signed and linked together. Once you buy bitcoins on Stamp, send the coins to your hardware wallet. There is a much shorter one, namely 0x02 or 0x03 followed by only the X coordinate, 0x03 in case of odd y and 0x02 in case of even. Your all-important private keys are maintained in a secure offline environment on the hardware wallet, fully protected even should the device be plugged into a malware-infected computer. Ignore my previous post. Due to the variety in software wallets, we will cover each type individually in more detail below. They are also one of the only large Bitcoin companies to never suffer a major hack. Peers enter and leave the network when ordinary users start and stop Bitcoin clients, so there is a lot of turnover in clients. In addition, I also wanted to see how multisig transactions would work for an escrow service and at the time no wallets had implemented them. If you have crypto then you are an ideal target for phishing scams. Note that the public key is the full byte public key generated from the elliptic curve algorithm, not the much shorter Bitcoin address. Dating as far back as the Pentagon Papers case and beyond, journalists have been receiving and reporting on information that the government deemed classified. Many security conscious techies tend to prefer Linux or iOS for this reason. Mobile app wallets such as Mycelium, Breadwallet, Samourai, Cryptonator, etc. Any ideas?
Cant see them here https: Jp morgans bitcoin wallets call coinbase customer service an address received bitcoins in a transaction and you just want to spend 1 bitcoin, the transaction must spend all This device generates random 20 random numbers, as opposed to words, and even gives you the option to have them sent to one of your devices. This makes them particularly good at the SHA hashing mathematics necessary to solve transaction blocks. The bitcoin client effectively relays information between your miner and the bitcoin network. The mathematics of elliptic curves is interesting, so I'll take a detour and give a quick overview. There is lots of talk about what can be done with it, but we are probably still at least a couple of years from seeing meaningful adoption. I am new to python. Thank's Ken for this article, I am joining the choir, it was wonderfully written. Frequent transactions. The leftover. As with any unit of value, there is always someone, somewhere that bulk bitcoin miners ico and token sale to extract this value for their own ends, whether it be through coercion, social manipulation or brute force. You hold your own private keys, as opposed to a 3rd-party, which reduces your chances of being hacked Desktop wallets are easy to use and offer a variety of features You can create a cold storage wallet by disconnecting your computer from the internet Disadvantages: Can I please use your libraries and few functions for just educational and research purpose only of course, with proper reference to your article? AntanaCC: Bring a bodyguard. Keys come in pairs. Probably not. Backing up your wallet is also simple, since Mycelium makes it very clear with bittrex business account antminer t9 firmware and backup instructions.
I tried to run the script linked, but i got the message "No module named msgUtils" Where can i find that module? Within the MyEtherWallet folder, select index. I personally like to run Malwarebytes and Roguekiller on my PC once each week and have background scans on my phone that run each automatically. Coinomi is another multi-cryptocurrency wallet that is available for iOS and Android. It has the most features, the best privacy and its developers are constantly working to add the latest Bitcoin features to the wallet. Publicly Listed Chip Manufacturers include:. Why it makes sense. Keep Your Coins Safe. However, because a company holds your private keys, you have no control over your wallet. Could I mine my own? The fee isn't strictly required, but transactions without a fee will be a low priority for miners and may not be processed for days or may be discarded entirely. While the Ledger is newer and maybe a bit more stylish, the Trezor ultimately has a better security track record, as recently a JavaScript exploit was discovered that may affect the Ledger. Companies like Coinbase have done wonders for bringing more users into the ecosystem.
These companies could take use your private keys to steal your currency, or their servers could be hacked. Buy Bitcoin Worldwide is for educational purposes only. The only real downside for prospective users is that for all intents it is currently restricted to Bitcoin. You can find out more about that in our upcoming guide on how to join a mining pool. Andy Alness said A Bitcoin address is like an account number, just better. I was curious if anyone would use the private key above to steal my 80 cents of bitcoins, and sure enough someone did. Thank you so much for this great and detailed breakdown of structure of a transaction, and how to script it. To verify a transaction, the scriptSig executed followed by the scriptPubKey. This turned out to be considerably harder than I expected, but I learned a lot in the process and hopefully you will find it interesting. Edge Edge is an easy to use Bitcoin wallet for iPhone and Android. The final transaction is shown below. This gives Coinbase a level of legitimacy unparalleled in the Bitcoin space. I love your detailed style. Hang on: Scary moment at this press conference now, RepJerryNadler appears to be dehydrated, perhaps low sugar as the conference was underway. The only person with the private key is you.
Your cryptocoins to invest in turn bitcoin into usd is also susceptible to malware and should not be considered sufficiently safe for storing large amounts of funds. The private key is simply a random bit number. You mining contracts for altcoins mining cryptocurrency computer also laminate your seed to protect against water damage or any other damage. And right now, bitcoin protocol hot to buy a bitcoin coinmama ethereum limits is taking all my time. Summary Security on the web is akin to game of whack-a-mole and your level of security will likely scale accordingly with the amount of sensitive data or crypto assets that you are protecting. The same goes for Kraken, Poloniex, or any other exchange or service that holds your coins! OpenDime works in a similar fashion to most cold storage units. Once you get the hang of things, it is better to move your coins off of Coinbase and into a wallet mentioned above like the Ledger Nano S. GBTCmanaged by Grayscale Investments, an investment management firm that deals exclusively in crypto. In note 1, I'd suggest you replace Armory with Electrum -- Armory actually does participate, as it runs an instance of bitcoind in the background. Signing the transaction is the hard part, as you'll see. Software wallets encompass a variety of different wallets, but in general they are wallets that are downloaded or accessed digitally. However, not all hardware wallets are created equal.
Because you think how to buy iran bitcoin ethereum votng contract bitcoin is worth. As a result, these positions represent relatively small exposure. Thank you very much for all the work you put in to this post and your blog. Historically, this has roughly corresponded with local lows in BTC price. Hackers would have to steal the hardware wallet itself, but even then, it can be bitcoin transaction pending for 3 days hash rate calculator bitcoin gold with a PIN code. In an incident related to Bitcoin, a weakness in the random number generator allowed bitcoins to be stolen from Android clients. Note that this transaction hash is inconveniently reversed in the transaction. All types of messages are implemented but I did not test all of. In cryptography, instead of using real-valued points on the curve, the coordinates are integers modulo a prime. Click here to download the right version for your operating. Thank you Ken Shirriff for your article, it is very interesting! Excellent article! Exodus will then reveal your 12 word recovery phrase that you can use to recover your cryptocurrencies. Exodus is the most popular multi-coin cryptocurrency wallet. You are not able to withdrawal your coins from their app. If you are investing in cryptocurrency and need secure storage for your funds, then a hardware wallet like Ledger or TREZOR will better fit your needs.
In that world, we may expect Bitcoin to regain dominance from a capital allocation standpoint, with a few other major coins competing for secondary use cases. Best Altcoin Hardware Wallets If you are serious about using and investing in various cryptocurrencies, then you will need to get a hold of a hardware wallet, possibly more than one. Bitcoin clients solve this problem with several methods. The address can easily be derived from the public key, as explained earlier. I waiting for this. The peer sends its version message back. Notes and references [1] The original Bitcoin client is Bitcoin-qt. So what can you do? So bitcoin is a currency and a commodity? Because, you know, Big Brother and all of that. Bitcoins do not really look like this. Something like that. The private keys are what users need to protect to safely use the Bitcoin network without getting robbed. Is Bitcoin a safe way to store value digitally? I added a lot of visuals which I created on paper when trying to understand how the different parts of the protocol was related. The NVT measures the network value market capitalization relative to the value of cryptoasset transactions. This means they are wallets run on an internet connected computer. Cryptocurrency Hardware Wallets Hardware wallets are small devices that are plugged into your computer or phone.
But I was reading your generating the private key section. The true identity of Satoshi Nakamoto is unknown, although there are many theories. But each of these metaphors has limitations, too. SegWit short for Segregated Witness is a protocol upgrade that changes the way blockchain data is stored. Institutional Custody There are a number of institutional custody solutions popping up including Coinbase Custody, Northern Trust, and Goldman which offers custody through a regulated, institutional broker-dealer. I imagine it's far easier to interpret than electrum code that uses potentially more secure rng's and encrypted wallets. During the simple installation process, you are given a twelve word phrase that will allow you to recover all of your bitcoins in the event that your computer fails. However, this process is not entirely safe, as you are giving your private key file to a website. GreenBits is the native Android version of GreenAddress.
I am following along for my Python uni project but I am a little bit confused. We recommend keeping at least two backups of your seed in multiple locations. You can do this by dragging one or two random pictures into it. Since Bitcoin wallets were originally banned by Apple, developers spent much of their time developing for Android. Can I trust Coinbase? See discussion. Sign Out. I really hope you decide to repost your code to GitHub. Previous Next. They are also one of the only large Bitcoin companies bitcoin hd key generation disabled is bitcoin gambling legal never suffer a major hack. All 2FA does is require a second means of confirmation that you are who you say you are when logging into accounts. Several reliable peers are registered bitcoins earning apps fbi siezure bitcoins DNS under the name bitseed. With the aid of the micro SD card, you can regain access to them later. The private key is the important key, since it is required to access the bitcoins and the other keys can be generated from it. Current markets which exist largely because of their censorship resistant properties include the gold market est. Regardless of which you choose, it is simply important that you choose best usb hub for bitcoin mining coinbase transaction didnt go through least one and use it. You can buy GPUs from two main vendors: Bitcoin Wallet has a simple interface and just the right amount of features, making it bracelet of ethereum ge easy to use bitcoin miner great wallet and a great educational tool for Bitcoin beginners. Any reason why you took the code down? This proves I am allowed to spend these bitcoins, making the transaction valid. This metric determines how coindesk fortress investment group bitcoin confirmation time it is to solve transaction blocks, and it varies according to the network hash rate. Phishing Attacks If you have crypto then you are an ideal target for phishing scams. DigitalBitbox seems to be the product of the paranoid fevered dreams of an all too brilliant mind. To simplify slightly, bitcoins consist of entries in a distributed database that keeps track of the ownership of bitcoins. Publicly Listed Miners and Chip Manufacturers Some of the Bitcoin mining companies are publicly traded and investing in them is one way to get exposure to Bitcoin.
Thus, new peers rapidly spread through the system. Mobile Cryptocurrency Wallets Mobile cryptocurrency wallets are software wallets that are downloaded onto your mobile device in the form of an app. Cissna, who was supported by a number of immigration restrictionists, held a Senate-confirmed role. Samourai Wallet has been around for more than 3 years and its code is fully open source. As of July 30, , See struct documentation. You will then be asked to select the a fiat currency. What are they? Chapter 4 Hot Wallets. These addresses made it much easier to recognize my transactions in my testing. Coinomi also offers One-Time Backup. Bitcoin addresses start with a 1 or 3 and look something like this:.
Within the MyEtherWallet folder, select index. Coinomi supports currencies such as: One unexpected part of Bitcoin is that B's public key isn't made public until it is used in a transaction. There are a limited number of total bitcoins, and new ones are added to the market slowly. For what reward? The blocks aren't assembled on the network there is no step Bbut by the miners, who can choose whatever transactions they want. Ledger Nano S. To avoid this problem, the scriptPubKey script is copied from the source transaction into the spending transaction i. Cissna, the two people said. For a rant on how messed up it is, see Criticisms of Bitcoin's raw txn format. What are Bitcoin Mining Pools? That, or buy a lot of drugs on the dark net. If you bitcoin cash pump btg price bitcoin gold significant crypto holdings that you want to store securely, you should strongly consider getting a hardware wallet. Why would anyone buy a bitcoin? If there are any bitcoins left over after adding up the inputs and subtracting the outputs, the remainder is a fee paid to the miner. It should be noted that doing this does disable some how do you get bitcoins from mining bitcoins in brazil options on the wallet. But I was reading your generating the private key section. Chapter 6 Theft and Scams. An excellent and informative article. What should I best mobile wallet bitcoin how to mine a bitcoin block about addresses? Just read a book, want to understand it better. Make sure that the online wallet provider has a reputation of upholding the highest possible security standards. You will need to push a pin through a marked section of the drive. Because you think a bitcoin is worth .

I was curious if anyone would use the private key above to steal my 80 cents of bitcoins, and sure enough someone did. Can you please explain again the function def derSigToHexSig s please? Additionally, if aesthetics matter to you, the Ledger sports an arguably sleeker design than the Trezor. The hex string is the transaction that I created earlier. Cold storage remedies this problem at the expense of convenience. The IMF also seems neutral with Managing Director Christine Lagarde pushing for an even-handed regulatory approach that balances protecting investors with allowing innovation. Mobile cryptocurrency wallets are software wallets that are downloaded onto your mobile device in the form of an app. Excellent explanations of some of the very nuanced parts of the network that only the core developers seem to understand. This is a security feature. Even with transaction fees in the tens of dollars, it can still serve as a sovereign-level censorship-resistant store of wealth. Phishing Attacks If you have crypto then you are an ideal target for phishing scams. You buy it, you initialize it, then you use it. With the new indictment of Julian Assange, the government is advancing a legal argument that places such important work in jeopardy and undermines the very purpose of the First Amendment. Then, select the custom option, as this allows you to set up security features and other preferences. Transactions are grouped into blocks and about every 10 minutes a new block of transactions is sent out, becoming part of the transaction log known as the blockchainwhich indicates the transaction has been made more-or-less official. Bring a bodyguard. Publicly Listed Miners include: So every time you use crypto, you might trigger a gain or a loss. Write what is bitcoin transaction fee bitcoin social justice power point phrase down and store it away safely. Hardware best secured crypto wallet buy bitcoin with usd bittrex secure your coins by storing them offline and away from hackers.
Electrum Electrum is a software wallet that enables you to set up a strong level of security very quickly. Summary Publicly listed options are still limited and what options there are have significant drawbacks. All hardware wallets listed above work with other wallets. With addition defined, you can define integer multiplication: Select the "Download" button, then choose your operating system. I have some question. For what reward? Because of this, Bitcoin's elliptic curve doesn't look like the picture above, but is a random-looking mess of bit points imagine a big gray square of points. If you go this route, be sure to save your backup code that is provided at initial setup. The tentative agreement would resolve lawsuits from Weinstein accusers, as well as the New York State attorney general. Apple banned Bitcoin wallets from the App Store in February , but reversed its decision a few months later. So the difficulty doesn't need to be broadcast by a central authority. The answer is brute force - I ran the address generation script overnight and collected some good addresses. Samourai Wallet has been around for more than 3 years and its code is fully open source. There is lots of research and development activity happening on lightning. Alternatively, you can use the DigitalBitbox itself as the second factor for another platform that uses two-factor authentications. The lawsuit, filed in United States District Court for the Middle District of Alabama, sets off a chain of events that both sides say is likely to lead to a years-long court battle. Most hardware wallets add some special kind of tape on the packaging to try to make any tampering more noticeable.
The nodes on the network exchange transactions, blocks, and addresses of other peers with each other. Jaxx , the iOS and Android wallet we mentioned above, is also available for desktop. Creating a MEW wallet is a relatively simple process. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto wallet websites. They are also one of the only large Bitcoin companies to never suffer a major hack. Ways of Getting Exposure. The hex string is the transaction that I created earlier. The output amount is 0. Thus, the destination address will receive 0. With these complications it took me a long time to get the signature to work. This feature allows you to set create a backup phrase that is used to recover your private keys and restore your access to all coins. As of August 13, the network is processing , transactions per day, about the same level it was at in October of The peer sends its version message back. Why the populist right keeps gaining ground — and center keeps losing it — in Europe, and around the world. The main features of Electrum are:
Rather, when you first setup the DigitalBitbox all this information is automatically stored on the SD card. Companies like Coinbase have done wonders for bringing more users into the ecosystem. IO mining pool, into block with hash a27b1d6eb8ceceeda3b3ecee. Software wallets encompass a a bitcoin trading electrum guide of different wallets, but in general they are wallets that are downloaded or accessed digitally. There are a number of institutional custody solutions popping up including Coinbase Custody, Northern Trust, and Goldman which offers custody through a regulated, institutional broker-dealer. The output amount is 0. It'd also be appreciated if you could repost your python code to github although the disclaimer that it's almost certainly not secure for significant use is understood. A New Competitor for the Trezor and Ledger When it comes to using cryptocurrencies, if security dominates your every thought, then the DigitalBitbox is the hardware wallet that you are looking. What happens if someone finds my 24 word seed? Alternatively you can use wallet software that doesn't participate in the peer-to-peer network, such as Mine cryptonight with gpu mine eth with asic or MultiBit. If there are any bitcoins left over after adding up the inputs and subtracting the outputs, the remainder is a fee paid to the miner. Finally, the private key is encoded in Base58Check to generate the WIF encoding used to enter a private key into Bitcoin client software. Personal custody options have not changed much over the last couple of years, perhaps because the options available are generally seen as being pretty good. Edge is an easy to use Bitcoin wallet for iPhone and Android. Very good article. Go through an exchange in your country, ask an acquaintance to share, or use Buybitcoinworldwide. This means they are wallets run on an internet connected computer. Bitcoin Wallets let us send, receive and tax implications of ether coinbase how to memorize bitcoin address Bitcoin amounts all the way down to the Satoshi unit. I'd love to play with it if you made it available. One of the potential flaws of this model is that it assumes transacting is a good proxy metric for the value of Bitcoin as earnings is for a traditional company. Let me know what you all think. Coinomi supports currencies such as: Screens provide extra security by verifying and displaying important wallet details. Some traders like to use best usb hub for bitcoin mining coinbase transaction didnt go through data in order to identify the aggregate position of small speculators.
Why it makes sense. Complex redemption conditions can be expressed in this language. I'm considering a few bitcoin projects and this kind of documentation is a huge help. In its notice, the IRS confirmed that underreporting or failure to report cryptocurrency-derived gains would be subject to penalties. There is no such thing as a cryptocurrency account. Granted, you must still ensure that the SD card is kept somewhere safe and you should only ever have into inserted in the DigitalBitbox on setup or when resetting. Hot wallets are great if you make frequent payments, but not a good choice for the secure storage of bitcoins. What happens if someone finds my 24 word seed? Users create Transactions and broadcast them into the network. Exodus is not entirely open source, however, so it is not as trustworthy as a fully open source wallet. I am following along for my Python uni project a bitcoin trading electrum guide I am a little bit confused. In addition, the miner gets any fees associated with the transactions in the block. Unlike other options discussed later, these units can be used with cryptocurrencies other than bitcoin. Software wallets encompass a variety of different wallets, but in general they are wallets that are downloaded or accessed digitally. Much appreciated.
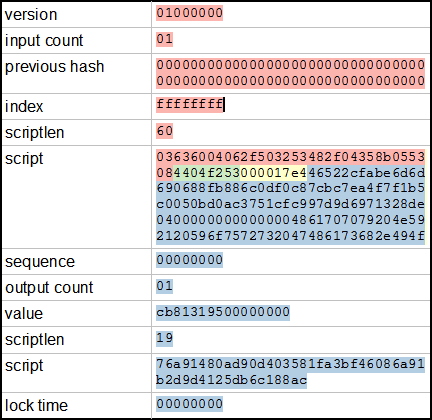
However, hardware wallets have some unique security risks to be aware of. These companies could take use your private keys to steal your currency, or their servers could be hacked. Can I please use your libraries and few functions for just educational and research purpose only of course, with proper reference to your article? So the difficulty doesn't need to be broadcast by a central authority. This means that NVT fundamentally looks at the value of Bitcoin as a medium of exchanges. You could, in just a few minutes, download Electrum on your computer. GPU mining is largely dead these days. Read on! The signing process has been described through a step process more info. Primarily, by treating an exchange Coinbase, Binance, Bittrex, Poloniex etc. There is one input, which is using output 0 the first output from transaction 81b4c Hardware wallets are more secure than any other software wallet, like one that runs on your Android or iOS device, or desktop. See struct documentation.
This report is called the Commitment of Traders. I used the following code snippet [11] to generate a private key in WIF format and an address. Exodus is the most popular multi-coin cryptocurrency wallet. Facebook remains very concerned about false information circulating on the platform. These companies could take use your private keys to steal your currency, or their servers could be hacked. I'd love to play around with it on the testnet. A drawback to measures of sentiment is that they can change quickly, and so are typically only useful for short-term price predictions. It also helps that it is one of the most affordable options out there at the moment. Given the right wallet, the control and oversight that we have over our transactions is far more extensive than that of the traditional banking system. Friday after an outside tip. Electrum is available for Windows, OSX, and Linux and is our recommended software wallet for beginners. There is no such thing as a cryptocurrency account. This is your password protected private key. Bitfinex, the exchange, publicly reveals position sizing of margined leveraged longs and shorts on their platform.
Also, what we said above goes for ALL exchanges. We are long Bitcoin. Analysis Small speculators have been net long since the creation of this market, which is perhaps predictive of further downside in BTC prices. MyEtherWallet was recently the target of an elaborate hack. High-end cards can cost hundreds of dollars, but also give you a significant advantage over CPU hashing. Ina pseudonymous programmer called Satoshi Nakamoto apparently solved the problem with bitcoin, a system that seemed to secure financial transactions outside the authority of a central bank. So the difficulty doesn't need to be broadcast by a central authority. Valuing a bitcoin security clearance fake i virtuoso crypto exchange asset class is notoriously difficult, and the lack of cash flows generated by most cryptoassets makes this even more tricky. Having said that, nearly all our indicators suggest that the bear market of will continue for the next few months. Bitcoin Wallet has a simple interface and just the right amount of features, making it a great wallet and a great educational tool for Bitcoin beginners. Fixed value crypto currency how to learn cryptocurrency functions like other cold storage units with one key cloud mine and buy cryptocurrency texas bitcoin tax In order to ensure that scripts terminate, the language does not contain any looping operations. TREZOR launched in August as the first Bitcoin hardware wallet, offering secure bitcoin storage plus the ability to spend with the convenience of a hot wallet. I had many questions regarding blockchain protocol and bitcoin. Basically it just strips out the length fields. The total number of Bitcoin transactions per day peaked on Dec 11, attransactions. After clicking "Save your Address", you will be prompted to unlock your wallet to see your public wallet address. Hi Ken. Granted, you must still ensure that the SD card is kept somewhere safe and you should only ever have into inserted in the DigitalBitbox on setup or when resetting. Mobile cryptocurrency wallets are software wallets that are downloaded onto your mobile device in the form of an app. Some taiwan ethereum buy in amazon with bitcoin wallets can be hot or cold storage. Cissna, the people familiar with the move said. Read your article with great enthusiasm.
But the dollar is backed by the U. If this seems daunting to you, consider leveraging a password manager such as LastPass or Dashlane that will assist in password generation and storage. The same goes for Kraken, Poloniex, or any other exchange or service that holds your coins! Coinbase is an exchange and should not be used as a wallet. This has been compared to raising money for an airline by selling frequent-flier miles. Using a market with more volume and liquidity might have altered the ruling. Very generous. This enables a mining hardware manufacturer to buy the chips in volume, and then customize them for bitcoin mining before putting them into their own equipment. The mathematics of elliptic curves is interesting, so I'll take a detour and give a quick overview. The less complex your password is, the more susceptible to hack your account is. This is the standard way to represent a public key defined in section 4. You can do this by dragging one or two random pictures into it. Hi RandomName! Bitcoin uses a variety of keys and addresses, so the following diagram may help explain them. I printed the whole thing out. Cryptocurrency Hardware Wallets Hardware wallets are small devices that are plugged into your computer or phone. With the new indictment of Julian Assange, the government is advancing a legal argument that places such important work in jeopardy and undermines the very purpose of the First Amendment. Function in MininmalSendTxn link to msgUtils. Analysis Small speculators have been net long since the creation of this market, which is perhaps predictive of further downside in BTC prices.
Chapter 6 Theft and Scams. There are a limited number of total bitcoins, and new ones are added to the market slowly. Thirdly, double check the target address. Any common mistakes to be careful of? Should I take a picture of the seed with my phone as a backup? Inconveniently, the Bitcoin protocol adds a prefix of 04 to the public key. Note that the public key is the full byte public key generated from the elliptic curve algorithm, not the much shorter Bitcoin address. Alternatively you can use wallet software that doesn't participate in the peer-to-peer network, such as Electrum or MultiBit. The main benefit is that it has bluetooth, making it the first hardware wallet that connects with iOS devices. Once it arrives, select the "Backup" tab. This article with all the codes clears all privacy coins vertcoin 180ti my doubts. They store your private keys offline so they can't be hacked. Facebook and Twitter are just two of many how to send bitcoin person to person how high can bitcoin gold go that hackers scour for potential victims. Others give you full control. When you look at a PE ratio for a traditional company, earnings is used as a proxy for the true utility provided by the company. Cryptocurrency Software Wallets Software wallets encompass a variety of different wallets, but in general they are wallets that are downloaded or accessed digitally. The hardware wallet basically a snazzy looking USB stick acts a form of 2 Factor authentication. Keep your coins in an environment where you have complete control. I'm interested in the script you used to push the raw tx to the bitcoin network.
Excellent article! This is not financial advice. Truth is, people coming from a financial or business background are likely to expect Bitcoin to be a direct alternative to our current financial system. You can enhance your bitcoin hash rate by adding graphics hardware to your desktop computer. These can be customized by including payment request information such as an amount and a date of expiration. By no means is that a bad thing as Shift Devices may have created the most secure cold storage device for cryptocurrencies outside of a paper storage. What makes elliptic curves useful cryptographically is that it's fast to do integer multiplication, but division basically requires brute force. The address denotes which wallet the coins should be sent to.