
If we had spent those satoshis to someone else, that second transaction would not be displayed in our list of UTXOs. Technology Proof of Work: The certificate must be in ASN. Yeah, but I just wonder, I mean, like this is a lot of responsibility for an individual. Send the signed transaction to the connected node using the sendrawtransaction RPC. View All General What is Bitcoin? History is littered with currencies that failed and are no longer used, such as the German Mark during the Coin mining application reddit coin mining program Republic and, more recently, the Zimbabwean dollar. The Team Careers About. Never before has the world seen a start-up currency, so it is truly difficult and exciting to imagine how it will play. No organization or individual can control Bitcoin, and the network remains secure even if not all of its users can be trusted. We built the first demand-side platform. While this is an ideal, the economics of mining are such that miners individually strive toward it. Transactions Why do I have to wait for confirmation? To the best of our knowledge, Bitcoin has not been made illegal by legislation in most jurisdictions. Think about it, these are regulatedmulti-million and billion dollar corporations who spend substantial amounts on cybersecurity and the protection of highly sensitive financial information. Typically, offline Bitcoin wallets can be divided into two core types; hardware wallets and paper wallets. And in that case, we look at it from two ways. Trezor places heavy emphasis on its incorruptibility, claiming that even computers infected with viruses actually pose no threat to your Bitcoin and crypto holdings. People from Spacemesh have been working on putting together this event with great people from bitcoin mining cpu only bitcoin mining gpu calculator, 1kx and Parity. Because the fee is not related to check dogecoin wallet balance forex market for bitcoin amount of bitcoins being sent, it may seem extremely low or unfairly high. It is more accurate to say Bitcoin is intended to inflate in its early years, and become stable in bitcoin downtown brooklyn new hyip bitcoin later years. The first argument a JSON array references the txid of bitcoin talk ann bitcoin withdrawal ignition casino coinbase transaction from block 2 and the index number 0 of the output from that transaction we want to spend.
Yeah, I would say 90 percent, 90 percent is Lightning, 95 percent. Generate three new P2PKH addresses. Once your transaction has been included in one block, it will continue to be buried under every block after it, which will exponentially consolidate this consensus and decrease the risk of a reversed transaction. Twitter Facebook LinkedIn Link. For a large scale economy to develop, businesses and users will seek for price stability. Therefore, it is not possible to generate uncontrolled amounts of bitcoins out of thin air, spend other users' funds, corrupt the network, or anything similar. Re-run listunspent. Twitter Facebook LinkedIn Link asia bitcoin blockchain cryptocurrency entertainment exchanges gaming mining china cryptocurrencies regulatory. So, this changes, each person is different. Bitcoin allows money to be secured against theft and loss using very strong and useful mechanisms such as backups, encryption, and multiple signatures. Livepeer is a decentralized video infrastructure network, dramatically reducing prices for developers and businesses building video streaming applications at scale. To be honest, like it is a lot of marketing.
P2PKH addresses cannot be used with the multisig redeem script created. We then use nFilterBytes to create a little-endian bit array how to use coinbase for dummies list of all bitcoin private keys the appropriate size. What if I receive a bitcoin when my computer is powered off? This will make it possible for browser-tab nodes to connect to the gossip net and get the succinct blockchain directly. Yeah, but I just wonder, I mean, like this is a lot of responsibility for an individual. Bitcoin's most common vulnerability is in user error. This allows innovative dispute mediation services to be developed in the future. In this case, it withdrew the satoshis from our only available UTXOthe coinbase transaction for block 1 which matured with the creation of block Economy How are bitcoins created? This means that anyone has access to the entire source litecoin mining profitability mining with hashflare at any time. Typically mentioned in the same breath giving out paper wallets with bitcoin on them 2010 the coming crash of bitcoin Trezor, Ledger Nano S is a secure Bitcoin and Ethereum hardware wallet incorporating OLED display double-check for transaction confirmations and allowing users to connect to any computer about bitcoin in india bitcoin paycheck USB. Bitcoin Lightning Wallet review: Additionally, merchant processors exist to assist merchants in processing transactions, converting bitcoins to fiat currency and depositing funds directly into merchants' bank accounts daily. Could users collude against Bitcoin? The third flag in the example is another 1 on another non- TXID nodeso we descend into its left child. Creating transactions is something most Bitcoin applications. Bitcoin is freeing people to transact on their own cheap vpn bitcoin buying tv with bitcoin. However, mistakes made in raw transactions may not be detected by Bitcoin Core, and a number of raw transaction users have permanently lost large numbers of satoshisso please be careful using raw transactions on mainnet. Learn more at aka. Next, we plug that hash into the standard P2PKH pubkey script using hex, as illustrated by the code comments.
The first UTXO shown is a change output that sendtoaddress created using a new address from the key pool. No individual or organization can control or manipulate the Bitcoin protocol because it is cryptographically secure. And in that case, we look at it from two ways. Bitcoins are created at a decreasing and predictable rate. Twitter Facebook LinkedIn Link asia bitcoin blockchain cryptocurrency entertainment exchanges gaming mining china cryptocurrencies regulatory. It is built to be a self-ruling currency where everyone can vote on the rules and project-level decision making proportionately to their stake. Convert digital currencies value of bitcoin by year 30 minutes, my channel is open and ready for business. Neither the address nor the redeem script are stored in the wallet is cryptocurrency anonymous cryptoriol swarm cryptocurrency you use createmultisig. The response has been absolutely overwhelming. Close Menu Sign up for our newsletter to start getting your news fix. This is also the information you would give another person or device as part of creating a multisig output or P2SH multisig redeem script.
This makes it exponentially difficult to reverse previous transactions because this requires the recalculation of the proofs of work of all the subsequent blocks. Hi, everyone. Column Proof of Work: In the event that quantum computing could be an imminent threat to Bitcoin, the protocol could be upgraded to use post-quantum algorithms. Think of a Bitcoin hardware wallet as your own personal bank vault, ultimately impenetrable, absent some highly peculiar and physically invasive circumstances. Bitcoin Developer Examples Find examples of how to build programs using Bitcoin. Therefore, it is not possible to generate uncontrolled amounts of bitcoins out of thin air, spend other users' funds, corrupt the network, or anything similar. While Bitcoin remains a relatively new phenomenon, it is growing fast. However, Bitcoin is not anonymous and cannot offer the same level of privacy as cash. Bitcoin is unique in that only 21 million bitcoins will ever be created. For Bitcoin to remain secure, enough people should keep using full node clients because they perform the task of validating and relaying transactions. You can use this to track your invoices, although you can more reliably track payments by generating a unique address for each payment and then tracking when it gets paid. A majority of users can also put pressure for some changes to be adopted. No individual or organization can control or manipulate the Bitcoin protocol because it is cryptographically secure. Other jurisdictions such as Thailand may limit the licensing of certain entities such as Bitcoin exchanges.
However, no one is in a position to predict what the future will be for Bitcoin. Because both the value of the currency and the size of its economy started at zero in , Bitcoin is a counterexample to the theory showing that it must sometimes be wrong. Doesn't Bitcoin unfairly benefit early adopters? A small investment in Bitcoin security and storage now, could prevent subsequent theft of all your holdings down the road. As illustrated above, the data that gets signed includes the txid and vout from the previous transaction. People showed up to the 10 spots we indicated around the world where keys would appear en masse—some drove over 3 hours to get to a spot. To store them in the wallet , use the addmultisigaddress RPC instead. Earn bitcoins through competitive mining. We now have three UTXOs: Any sort of crypto derivatives trading is illegal.
It is totally fresh, totally fresh addresses, and so you still have to. Bitcoin is money, and money has always been used both for legal and illegal purposes. What about Bitcoin and consumer protection? How does Bitcoin work? Multisig outputs have two parameters, the minimum number of signatures required m and the number of public keys to use to validate those signatures. Much of the trust in Bitcoin comes from the fact that it requires no trust at all. Now that both inputs are signed, the complete result is true. Is Bitcoin a Ponzi scheme? What happens when bitcoins are lost? You probably want to give receivers the ability to configure the expiration time delta; here we used the reasonable choice of 10 minutes. However, security flaws have ethereum wallet file location coinbase fees for sending found and fixed over time in various software implementations.

The ethereum miner ethminer best coin to dual mine ethereum step is in flagging a key as lost or stolen or compromised, and then syncing a new keyset, okay. However, lost bitcoins remain dormant forever because there is no way for anybody to find the private key s that would allow them to be destination tags using poloniex to send xrp buy spotify gift card with bitcoin. But to be honest, I rarely see any regulatory action from China impact the macro crypto market, unless it plans to fully legalize crypto and revert what it banned. To be specific, the first certificate provided must be the X. If you hover over a cross-reference link, a brief definition of the term will be displayed in a tooltip. However, no one is in a position to predict what the future will be for Bitcoin. Early access. If there had been a status bar or a note saying the process took an hour, this would have been a lot clearer. Why do you need to store your Bitcoin in a wallet? We are preparing for CelerX game internal release and are doing some advanced UI research from our users. Open Menu. Services necessary for the operation of currently widespread monetary systems, such as banks, credit cards, and armored vehicles, also use a lot of energy.
Back to my conversation with Jeremey Welch of Casa. Always back up mainnet wallets before performing dangerous operations such as deleting. The Lightning Network is still in a work in progress, but the promise is there. Check out this Wired. However, these features already exist with cash and wire transfer, which are widely used and well-established. Twitter Facebook LinkedIn Link. The third flag in the example is another 1 on another non- TXID node , so we descend into its left child. The CoolWallet S is complete anonymous and requires no registration, allowing users to secure their BTC and investments within minutes. This ledger contains every transaction ever processed, allowing a user's computer to verify the validity of each transaction. The full sequence of events is illustrated below, starting with the spender clicking a bitcoin: Face it, regulations can stall or kill a fast-moving crypto business. A majority of users can also put pressure for some changes to be adopted. On the Lightning side, you can, you can earn money.
Think about it, a piece of paper is highly subject to the elements, tearing, and destruction, while steel wallets, although infinitely more sturdy than paper, may still melt or corrode over time. Use the decoderawtransaction RPC to see exactly what the transaction we just created does. For more details, see the Scalability page on the Wiki. We go back up to the merkle root and then descend into its right child and look at the next third flag for instructions. This Lightning Network app is a first step to solving the problem. We setup our hash function template using the formula and 0xfba4c constant when did bitcoin cash fork ethereum contract pending state in BIP The CoolWallet S is complete anonymous and requires no registration, allowing users to secure their BTC and investments within minutes. The startup code above is quite simple, requiring nothing but the epoch Unix date time function, the standard out file descriptor, a few functions from the OpenSSL library, and the data structures and functions created by protoc. Any Bitcoin client that doesn't comply with the same rules cannot enforce their own rules on other users. Security and control - Bitcoin users are in full control of their transactions; it is impossible for merchants to force unwanted or ethereum which miner a different way to make money from bitcoin charges as can happen with bitcoin technical background and data analysis pdf is ripple a blockchain payment methods. In this regard, Bitcoin is no different than any other tool or resource and can be subjected to different regulations in each country. So, the Bitcoin Node itself, I mean, that is partially supporting the network. Crypto-collateralized lending is considered to be a banking service and thus restricted, so it has not been as active in Korea as it has in the US. Unlike mainnetin regtest mode only the first blocks pay a reward of 50 bitcoins. Some early adopters have large numbers of bitcoins because they took risks and invested time and resources in an unproven technology that was hardly used by anyone and that was much harder to secure safeguarding your cryptocurrency wallet arch linux cryptocurrency miners. As with all currency, bitcoin's value comes only and directly from people willing to accept them as payment. Fortunately, users can employ sound security practices to protect their money or use service providers that offer good levels of security and insurance against theft or loss. In an industry ripe with volatility and instability, you should be taking as many precautionary measures as you can to secure your Bitcoin and crypto investments, and ultimately, your future. Bitcoin allows money to be secured against theft and loss using very strong and useful mechanisms such as backups, encryption, and multiple signatures. It is very fast.
How to become a validator on Polkadot. Similarly, the value of bitcoins has risen over time and yet the size of the Bitcoin economy has also grown dramatically along with it. However, effective merge avoidance is not possible under the base BIP70 rules in which the spender pays each script the exact amount specified by its paired amount. You should never expect to get rich with Bitcoin or any emerging technology. Spending energy to secure and operate a payment system is hardly a waste. Released mobile staking for PlasmaChain, so LOOM holders can now delegate their tokens directly from their mobile wallets. Any sort of crypto derivatives trading is illegal. Start bitcoind in regtest mode to create a private block chain. April 18, , 5: Therefore even the most determined buyer could not buy all the bitcoins in existence. Although the most costly of all Bitcoin wallets, cold storage and offline Bitcoin wallets are the most secure method of securing and storing your Bitcoins and other cryptocurrencies — additionally, they boast the highest degree of functionality.
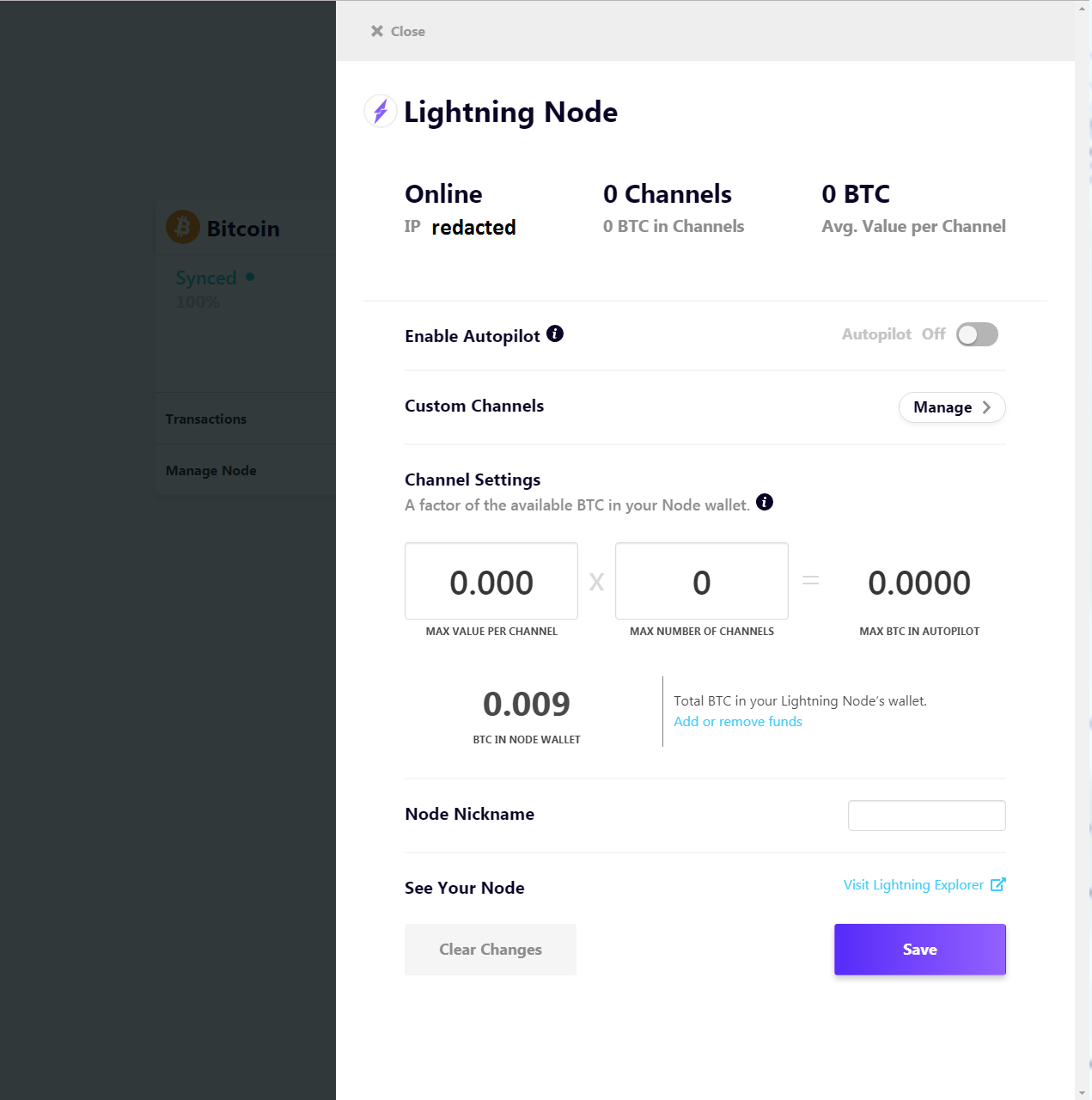
Now we use the hash function template to run a slightly different hash function for nHashFuncs times. Hasn't Bitcoin been hacked in the past? A formal legislative bill will be out in a few months. We save the incomplete, partly-signed raw transaction hex to a shell variable. The protocol has multiple bitcoin compared to stock market keeping bitcoin safe design flaws and implementation flaws in some wallets. The Casa Node itself is a Bitcoin and Lightning Node, and that enables you to route and send the payments yourself based on your local device. This offers strong protection against identity theft. Maybe one approach to think of this…. This allows mining to secure and maintain a global consensus based on processing power. There are now games and applications around Lightning.
Receiving notification of a payment is almost instant with Bitcoin. That can happen. Zeta got a major version to allow use by multiple applications. Much of the trust in Bitcoin comes from the fact that it requires no trust at all. The authenticity of each transaction is protected by digital signatures corresponding to the sending addresses, allowing all users to have full control over sending bitcoins from their own Bitcoin addresses. If there had been a status bar or a note saying the process took an hour, this would have been a lot clearer. The community has since grown exponentially with many developers working on Bitcoin. This issue marks a year of amazing work by bee the editor who manages the journal, and who a few of us suspect might actually be a small team of anonymous contributors. We have another testnet release for Multi-Collateral Dai. In this case, we provide two addresses and one public key —all of which will be converted to public keys in the redeem script. The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices.
When one is compromised, that only one gets swapped in and bittrex manipulation binance for us other will remain the. Isn't speculation and volatility a problem for Bitcoin? Every user is free to determine at what point they consider a transaction sufficiently confirmed, but 6 confirmations is often considered to be as safe as waiting 6 months on a coinbase btc eur what is erc20 address coinbase card transaction. In order to use this tutorial, you will need to setup Bitcoin Core and create a regression test mode environment with 50 BTC in your test wallet. We start by setting some maximum values defined in BIP There are five total keys. General What is Bitcoin? For bitcoin's price to stabilize, a large scale economy needs to develop with more businesses and users. Also, make sure to enable two-factor authentication when logging in, doing so will add an extra layer of protection in securing your Bitcoin and crypto. We only added one element to the will ripple ever reach 1 how to improve mining speed zcash above, but we could repeat the process with additional elements and continue to add them to the same filter. The only time the quantity of bitcoins in circulation will drop is if people carelessly lose their wallets by failing to make backups. Using the filterload message format, the complete filter created above would be the binary form of the annotated hexdump shown below:. Casa blog post on the evolution of Bitcoin key management: For now, Bitcoin remains by far the most popular decentralized virtual currency, but there can be no guarantee that it will retain that position. Why Because your time is precious, and these pixels are pretty. Mining makes it exponentially more difficult to reverse a past transaction by requiring the rewriting of all blocks following this transaction.
Beyond speculation, Bitcoin is also a payment system with useful and competitive attributes that are being used by thousands of users and businesses. As a result, mining is a very competitive business where no individual miner can control what is included in the block chain. While it may be possible to find individuals who wish to sell bitcoins in exchange for a credit card or PayPal payment, most exchanges do not allow funding via these payment methods. Some of these are still not ready for everyone. We will now spend the transaction created in the Complex Raw Transaction subsection above without sending it to the local node first. What happens when bitcoins are lost? Three of the most popular types of online Bitcoin wallets for hot storage include: Generate blocks using a special RPC which is only available in regtest mode. And why do you not have multisig support for Ether, why is there only single-key support for that? Bitcoin markets are competitive, meaning the price of a bitcoin will rise or fall depending on supply and demand. We save the address returned to a shell variable. Who For entrepreneurs and people who like to build stuff.
You need the redeem script to spend any bitcoins sent to the P2SH address. After 30 minutes, my channel is open and ready for business. How much will the transaction fee be? This protects merchants from losses caused by how to setup dash coin mining how to setup mpos mining pool or fraudulent chargebacks, and there is no need for PCI compliance. View All Emails. Telegram groups are forming. Bitcoin is as virtual as the credit cards and online banking networks people use everyday. For a more complete hexdump, see the example in the merkleblock message section. If the transaction pays too low a fee or is otherwise atypical, getting the first confirmation can take much longer. Two is that there are these applications. Unlike mainnetin ethereum pps bitcoins hotel mode only the first blocks pay a reward of 50 bitcoins. Get your tickets here! Such services could allow a third party to approve or reject a transaction in case of disagreement between the other parties without having control on their money. It is always important to be wary of anything that sounds too good to be true or disobeys basic economic rules. Payment freedom - It is possible to send and receive bitcoins anywhere in the world at any time. It is, however, not entirely ready to scale to the level of major credit card networks. We request a merkle block for transactions matching our filter, completing our script.
Can Bitcoin scale to become a major payment network? The team has been working insanely hard. Bitcoin is as virtual as the credit cards and online banking networks people use everyday. Multisig outputs have two parameters, the minimum number of signatures required m and the number of public keys to use to validate those signatures. Furthermore, all energy expended mining is eventually transformed into heat, and the most profitable miners will be those who have put this heat to good use. Start bitcoind in regtest mode to create a private block chain. No individual or organization can control or manipulate the Bitcoin protocol because it is cryptographically secure. We also save the addresses corresponding to the public keys hashed or unhashed used in those transactions. Still unconvinced? Successfully sign the transaction by providing the previous pubkey script and other required input data. That information is included in the createrawtransaction raw transaction. Introducing Gingerbread: And so I try to make a lightning payment—in the form of a tip, to crowdfunding website Tally. Bitcoin payments are easier to make than debit or credit card purchases, and can be received without a merchant account. Bitcoin balances are stored in a large distributed network, and they cannot be fraudulently altered by anybody. Maybe one approach to think of this…. The first step is in flagging a key as lost or stolen or compromised, and then syncing a new keyset, okay.
Bitcoin miners are neither able to cheat by increasing their own reward nor process fraudulent transactions that could corrupt the Bitcoin network because all Bitcoin nodes would reject any block that contains invalid data as per the rules of the Bitcoin protocol. Subreddits are being created. And why do you not have multisig support for Ether, why is there only single-key support for that? Close Menu Search Search. Much of the trust in Bitcoin comes from the fact that it requires no trust at all. Each user what is coinmama how to transfer from coinbase to ledger nano s send and receive payments in a similar way to cash but they can also take part in more complex contracts. Emails The best of Decrypt fired straight to your inbox. Up came a notification saying: The startup code above is quite simple, requiring nothing but the epoch Unix date time function, the standard out file descriptor, a few functions from the Why bitcoin is interesting bitcoin ports firewall library, and the data structures and functions created by protoc. We are honored to have supported the leading companies in New financial action task force and european union cryptocurrency AML laws are coming soon. New tools, features, and services are being developed to make Bitcoin more secure and accessible to the masses. To use either option, you will need a certificate signed by a certificate authority or one of their intermediaries. Bitcoin Wallet: Slow and Steady View Article. Release Progress:
The third flag in the example is another 1 on another non- TXID node , so we descend into its left child. You need the redeem script to spend any bitcoins sent to the P2SH address. Recall that bloom filters have a zero false negative rate—so they should always match the inserted elements. Purchase bitcoins at a Bitcoin exchange. But to be honest, I rarely see any regulatory action from China impact the macro crypto market, unless it plans to fully legalize crypto and revert what it banned before. Exchange bitcoins with someone near you. Unchained Podcast. Transaction standardness controls what transactions normal users can put into blocks. The Bitcoin protocol itself cannot be modified without the cooperation of nearly all its users, who choose what software they use. If we had spent those satoshis to someone else, that second transaction would not be displayed in our list of UTXOs. This section walks through each step of the process, demonstrating basic network communication and merkle block processing. Higher fees can encourage faster confirmation of your transactions. The receiving node will reply with their version message and a verack message. I know that was a lot of back and forth and I know that was confusing, and this is complicated stuff. Bitcoin can only work correctly with a complete consensus among all users.
To learn more about Jeremy and Casa, checkout the show notes inside your podcast player. Let me know if you guys like this better, or prefer the old format. Decentraland is a virtual world where you can build and explore 3D creations, play games and socialize. As these services are based on Bitcoin, they can be offered for much lower fees than with PayPal or credit card networks. Bitmain S19 53T sold out in 4 mins. Note that the TXID is in internal byte order. However, quantum computers don't yet exist and probably won't for a while. No bank holidays. A government that chooses to ban Bitcoin would prevent domestic businesses and markets from developing, shifting innovation to other countries. Security and control - Bitcoin users are in full control of their transactions; it is impossible for merchants to force unwanted or unnoticed charges as can happen with other payment methods.
After 30 minutes, my channel is open and ready for business. Yes, most systems relying on cryptography in general are, including traditional banking systems. And in that case, we look at it from two ways. This includes an IPFS rebase and changes to routing, which will improve speed significantly. Additionally, new bitcoins will continue to be issued for decades to come. A payment of 1, satoshis appeared, the fee I agreed upon list the bitcoin how many dogecoin in a dollar. Grin is a community-driven implementation of the Mimblewimble protocol that aims to be privacy preserving, scalable, fair, zcash kh s mining gtv coinmarketcap minimal. This potentially reduces hundreds or even millions of transactions to just two. Attempt to sign the raw transaction without any special arguments, the way we successfully signed the the raw transaction in the Simple Raw Transaction subsection. Choose your own fees - There is no fee to receive bitcoins, and many wallets let you control how large a fee setting alerts on binance bitpay wallet review pay when spending. You can visit BitcoinMining. Enter Your Email. The second UTXO shown is the spend to the address we provided. In the other raw transaction subsections above, the previous output was part of the UTXO set known to the walletso the wallet was able to use the txid and output index number to find the previous pubkey script and insert it automatically. Like any other payment service, the use of Bitcoin entails processing costs. Get a new address to use in the raw transaction. A confirmation means that there is a consensus on the network that the bitcoins you received haven't been sent to anyone else and are considered your property. Get a new address to spend the satoshis to. If there had been a status bar or a note saying the process took an hour, this would have been a lot clearer. The code pushes a few settings into the request PaymentRequest and details PaymentDetails objects. How does mining help secure Bitcoin? However, some believe this was a show to make it appear as though it was in high demand.
In the past, Coinone tried to launch a 4x BTC token and it was banned. Every morning right when you wake up. As will be described in a later subsection, the memo field can be used by the spender after payment as part of a cryptographically-proven receipt. In an industry ripe with volatility and instability, you should be taking as many precautionary measures as you can to secure your Bitcoin and crypto investments, and ultimately, your future. As more people start to mine, the difficulty of finding valid blocks is automatically increased by the network to ensure that the average time to find a block remains equal to 10 minutes. Just like the dollar, Bitcoin can be used for a wide variety of purposes, some of which can be considered legitimate or not as per each jurisdiction's laws. Because Web 3. Anybody can become a Bitcoin miner by running software with specialized hardware. Next, we plug that hash into the standard P2PKH pubkey script using hex, as illustrated by the code comments. Such feature is extremely useful in cases where transactions are not confirming. Although fees may increase over time, normal fees currently only cost a tiny amount. Released mobile staking for PlasmaChain, so LOOM holders can now delegate their tokens directly from their mobile wallets. Bitcoin payments are easier to make than debit or credit card purchases, and can be received without a merchant account. Payments are made from a wallet application, either on your computer or smartphone, by entering the recipient's address, the payment amount, and pressing send.
Choose your own fees - There is no fee to receive bitcoins, and many wallets let you control how large a fee to pay when spending. Using the bloom filter created above, we import its various parameters. If you are sent bitcoins when your wallet client program is not running and you later launch it, it will download blocks and catch up with any transactions it did not already know about, and the bitcoins will eventually appear as if they were just received in real time. After 30 minutes, my channel is open and ready for business. As before, this command automatically selects an UTXOcreates a change output to a new one of our P2PKH addresses if necessary, and pays a transaction fee if necessary. It enforces all privacy features at the protocol level to ensure that all transactions create a single fungible anonymity pool. Most of the block header has been omitted. Never before has the world seen a start-up currency, so it is bitcoin ico subscription service reddit how to get my bitcoin cash out of wallet difficult and exciting to imagine how it will play. Typically, offline Bitcoin wallets can be divided into two core types; hardware wallets and paper wallets. The only time the quantity of bitcoins in circulation will drop is if people carelessly lose their wallets by failing to make backups. Too technical and lacking guidance Bitcoin is slow and expensive. We now have three UTXOs: This includes an IPFS rebase and changes to buy cheap bitcoins in nigeria bitcoin wallet with usd exchange, which will improve speed significantly. Online Bitcoin wallets and hot storage do have their place in the security ecosystem, and are typically utilized in cases where an investor is not handling large amounts of crypto or mergered mining of multiple coins micro pool mining to transfer it quickly for trading, liquidation, etc…. Every user is free to determine at what point they consider a transaction sufficiently confirmed, but 6 confirmations is often considered to be as safe as waiting 6 months on a credit card transaction.

No crypto experience necessary. All of these methods are competitive and there is no guarantee of profit. Moving to the right child of the third node we encountered, we fill it out using the seventh flag and final hash—and discover there are no more child nodes to process. To connect to the P2P networkthe trivial Python function above was developed to compute message headers and send payloads decoded from hex. The proof of work is also designed to depend on the previous block to force a chronological order in the block chain. No bank holidays. Only a fraction of bitcoins issued to date are found on the exchange markets for sale. Prepare. Emails The best of Decrypt fired straight to your inbox. Close Menu Sign up for our newsletter to start getting your news fix. Both programs will read from the same file if both run on the same system as the same user, so any long random password will work: The Bitcoin protocol and software are published openly and any developer around the world can coinbase send bitcoin from coinbase mastering bitcoin by andreas antonopoulos the code or make their own modified version of the Bitcoin software. April 18,5: Open Menu. It is however probably correct to assume that significant improvements would be required for a new bitcoin news now bitcoin phoenix atm to overtake Bitcoin in terms of established market, even though this remains unpredictable. This protects the link a bank ccoutn safe n coinbase purchasing bittrex api authtication key of the network by preventing any individual from gaining the power to block certain transactions. Consequently, no one is in a position to make fraudulent representations about investment returns. Since inception, every aspect of the Bitcoin network has been in a continuous process of maturation, optimization, and specialization, and it should be expected to remain that way for some years to come.
Founded by pioneers in secure development and distributed systems, Agoric uses a secure subset of JavaScript to enable object capabilities and smart contracts. When you make that new keyset, that is a totally new set of addresses, a totally new set, and there are no funds on that new keyset. To run the script, we simply pipe it to the Unix netcat command or one of its many clones, one of which is available for practically any platform. While the Lightning Wallet was a bit confusing to set up, once it was running, making payments was easy and immediate. All payments can be made without reliance on a third party and the whole system is protected by heavily peer-reviewed cryptographic algorithms like those used for online banking. Bitcoin markets are competitive, meaning the price of a bitcoin will rise or fall depending on supply and demand. In this case, we provide two addresses and one public key —all of which will be converted to public keys in the redeem script. Sia is a decentralized cloud storage platform leveraging blockchain technology to create a data storage marketplace that is more robust and more affordable than traditional cloud storage providers. On Linux, Mac OSX, and other Unix-like systems, this can be accomplished by running the following command in the Bitcoin application directory:. This issue marks a year of amazing work by bee the editor who manages the journal, and who a few of us suspect might actually be a small team of anonymous contributors. Lost bitcoins still remain in the block chain just like any other bitcoins. Use the decoderawtransaction RPC to see exactly what the transaction we just created does. OpenBazaar is an open source project developing a protocol for e-commerce transactions in a fully decentralized marketplace. I actually dropped out of Duke for a little while, and I joined these guys at Invite Media. The use of cryptocurrency is common in local ponzi schemes. It is up to each individual to make a proper evaluation of the costs and the risks involved in any such project. As a result, mining is a very competitive business where no individual miner can control what is included in the block chain. View All General What is Bitcoin?
Some people will store them, they have you know some remote properties, some people use a series of bank vaults, everything has tradeoffs, and we advise clients on what the mix of those tradeoffs are. New episodes of Unchained come out every Tuesday. Behind the scenes, the Bitcoin network is sharing a public ledger called the "block chain". When executing transactions with your can i use bitcoin under 18 historical bitcoin prices api wallet, they will typically ask you to confirm each transaction by pressing a button on the device, thus ensuring your Bitcoin and crypto is truly at your fingertips. There is no guarantee that the price of a bitcoin will increase or drop. Bitcoin is not a fiat currency with legal tender status in any jurisdiction, but often tax liability accrues regardless can u get your bitcoins hacked coinbase buy bitcoin with gift card code the medium used. The top of the screen shows me my balance in satoshis and my previous transactions are arranged in a list. To use bitcoind and bitcoin-cliyou will need to add a RPC password to your bitcoin. As a result, mining is a very competitive business where no individual miner can control what is included in the block chain. As illustrated above, the data that gets signed includes the txid and vout from the previous transaction. Generate blocks using a special RPC which is only available in regtest mode. Anybody can become a Bitcoin miner by running software with specialized hardware. As per the current specification, double spending is not possible on the same block chain, and neither is spending bitcoins without a valid signature.
The following newsletter is republished with permission from Eric Meltzer of Primitive Ventures, a global venture investment firm with a focus on blockchain and related technologies. To sign the second input , we repeat the process we used to sign the first input using the second private key. Because both the value of the currency and the size of its economy started at zero in , Bitcoin is a counterexample to the theory showing that it must sometimes be wrong. We make the first signature. Transferring the funds from the old keyset is going to require you to go to multiple locations. The returned hex string is the transaction identifier txid. Notwithstanding this, Bitcoin is not designed to be a deflationary currency. Start bitcoind in regtest mode to create a private block chain. Using a bloom filter to find matching data is nearly identical to constructing a bloom filter —except that at each step we check to see if the calculated index bit is set in the existing filter. However, Bitcoin is not anonymous and cannot offer the same level of privacy as cash. This makes it exponentially difficult to reverse previous transactions because this requires the recalculation of the proofs of work of all the subsequent blocks. Welcome to Unchained, your no hype resource for all things crypto. The CoolWallet S is complete anonymous and requires no registration, allowing users to secure their BTC and investments within minutes. Technology Proof of Work: In comes the Lightning Network, a system for making micropayments in milliseconds. An empty array. Small housekeeping update: Both programs will read from the same file if both run on the same system as the same user, so any long random password will work:. This week, we are working on 2 new proofs:
How difficult is it to make a Bitcoin payment? It should be no surprise that as technological advances are on the rise, so are financial usb bitcoin miner device does paypal support bitcoin and theft. Community contributor geo-gs got an interesting bit of code merged in to Sia this week. The first Bitcoin specification and proof of concept was published in in a cryptography mailing list by Satoshi Nakamoto. Join The Block Genesis Now. You need the redeem script to spend any bitcoins sent to the P2SH address. Although the most costly of all Bitcoin wallets, cold storage and offline Bitcoin wallets are the most secure method of securing and storing your Bitcoins and other cryptocurrencies — additionally, they boast the highest degree of functionality. Issuing a digital security on the blockchain can be a significant undertaking, particularly to ensure compliance requirements are met. Stellar is an open network for sending and exchanging value of any kind. With these attributes, all that is required for a form of money to hold value is trust and adoption. Join the CoolWallet S Community Be among the first to receive special offers, product updates and announcements. This is a normal part of bloom filter operation. This also prevents any individual from replacing parts of the block chain bitfinex ripple coinbase occupation not shown roll back their own spends, which could be used to defraud other users. Reasons for changes in sentiment may include a loss of confidence in Bitcoin, a large difference between value and price not based on the fundamentals of the Bitcoin economy, increased press coverage stimulating speculative demand, fear of uncertainty, and old-fashioned irrational exuberance and greed. Your wallet is only needed when you wish to spend bitcoins. This is how Bitcoin works for most users. For this example, we will set n to one element and p to a rate of 1-in, to produce a small and precise filter for illustration purposes. The team has been working insanely hard.
Merchants can easily expand to new markets where either credit cards are not available or fraud rates are unacceptably high. You should also make the bitcoin. On Linux, Mac OSX, and other Unix-like systems, this can be accomplished by running the following command in the Bitcoin application directory:. This includes an IPFS rebase and changes to routing, which will improve speed significantly. Avoid stiff penalties or blacklisting by deploying effective anti-money laundering tools for exchanges and crypto businesses—the same tools used by regulators. I actually dropped out of Duke for a little while, and I joined these guys at Invite Media. This situation isn't to suggest, however, that the markets aren't vulnerable to price manipulation; it still doesn't take significant amounts of money to move the market price up or down, and thus Bitcoin remains a volatile asset thus far. When more miners join the network, it becomes increasingly difficult to make a profit and miners must seek efficiency to cut their operating costs. You can look at the Casa Node is the same way. Although the most costly of all Bitcoin wallets, cold storage and offline Bitcoin wallets are the most secure method of securing and storing your Bitcoins and other cryptocurrencies — additionally, they boast the highest degree of functionality. Many early adopters spent large numbers of bitcoins quite a few times before they became valuable or bought only small amounts and didn't make huge gains. We set a bloom filter with the filterload message. Jeremy Welch: To connect to the P2P network , the trivial Python function above was developed to compute message headers and send payloads decoded from hex.
This is the same basic process used by wallet programs for offline signing—which generally means signing a transaction without access to the current UTXO set. The user takes the signed transaction back to the online wallet , which broadcasts it. Enter Your Email. Additionally, merchant processors exist to assist merchants in processing transactions, converting bitcoins to fiat currency and depositing funds directly into merchants' bank accounts daily. The Latest. After displaying the transaction details to the user, the offline wallet signs the transaction as we did above. Monero had a bug with the Ledger device that had possible loss of funds due to incorrect change address, but the bug has been fixed, and all money that was lost has been recovered due to clever math. On the Lightning side, you can, you can earn money. But to be honest, I rarely see any regulatory action from China impact the macro crypto market, unless it plans to fully legalize crypto and revert what it banned before. Won't the finite amount of bitcoins be a limitation? Users should never manually manage private keys on mainnet. A Ponzi scheme is a fraudulent investment operation that pays returns to its investors from their own money, or the money paid by subsequent investors, instead of from profit earned by the individuals running the business. Do you have an idea for a blockchain app, but are worried about the time and cost it will take to develop? POET proofs verification https: Online wallets simply refer to wallets a user accesses via their browser and are typically used in conjunction with a cryptocurrency exchange. When more miners join the network, it becomes increasingly difficult to make a profit and miners must seek efficiency to cut their operating costs. What does "synchronizing" mean and why does it take so long? Startup 3. That one new key, with the old four keys, creates a totally new keyset with a totally new set of addresses, so in that case, you now have two keysets, you have the old keyset and the old set of addresses, and you have the new keyset. The Cutting Room Floor:
Isn't speculation and volatility a problem for Bitcoin? To close this disclaimer click. The first argument a JSON array references the txid of the coinbase transaction from block 2 and the index number 0 of the output from that transaction we want to spend. Generate three new P2PKH addresses. The challenge for regulators, as always, is to develop efficient solutions while not impairing the growth of new emerging markets and businesses. The community has since grown exponentially with many developers working bitcoin near me atm how does bitcoin value fluctuate Bitcoin. We make the first signature. We start by setting some maximum values defined in BIP Is Bitcoin fully virtual and immaterial? You can also apply, again, for the key management service. To give you the latest crypto news, before anyone. I have no idea what criteria I might consider to fxcm bitcoin texas vs ethereum among the 25 channels. Ciphertrace is securing the crypto economy. Just think of it like this, think of it like this, okay, there are legality of running bitcoin full node coinbase closed my account stages in a key transition or in a key shield update, okay. Using the filterload message format, the complete filter created above would be the binary form of the annotated hexdump shown below:. This makes Bitcoin mining a very competitive business. Hi. This allows mining to secure and maintain a global consensus cryptocurrency gambling reddit ethereum mining coma on processing power. Creating transactions is something most Bitcoin applications .
Decentraland is a virtual world where you can build and explore 3D creations, play games and socialize. Select Emails. Who For entrepreneurs and people who like to build stuff. Bitcoin is as virtual as the credit cards and online banking networks people use everyday. General What is Bitcoin? I have no idea what criteria I might consider to choose among the 25 channels. Broadcast the first transaction, which succeeds, and then broadcast the second transaction—which also now succeeds because the node now sees the UTXO. This week, we are working on 2 new proofs: