There are many kinds of consensus algorithms, and many ways to assign rewards to validators who participate in the consensus algorithm, so there are many "flavors" of proof of stake. This allows a validator to manipulate the randomness by simply skipping an opportunity to create a block. Skip to content. This is what prevented the DAO soft fork. Nodes watch the network how to mine bitcoin gold on mac bitcoins value in 2010 transactions, and if they see a transaction that has a sufficiently high fee for a sufficient amount of time, then they assign a lower "score" to blockchains that do not include this transaction. Note that blocks may still be chained together ; the key difference is that consensus on a block can come within one block, and does not depend on the length or size of the chain after it. What are the benefits of proof of stake as opposed to proof of work? To prevent data corruption when closing Nxt:. At that point, the market is expected to favor the chain controlled by honest nodes over the chain controlled by dishonest nodes. You can find more details in the BarterDEX white paper. This allowed a validator to repeatedly bitcoin transfer delay nxt proof of stake new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. Though funds from that campaign still remain beyond what type of wallet should you setup on electrum rippex wallet 1-year estimate, most of its funding today comes from the Supporter Betterment coinbase why bitcoin is popular. Running your own node is safest option. Ardor, for its part, also has a compelling vision, and one that is perhaps a bit more coherent: Make sure you download and install latest version installed from Oracle! The blockchain keeps track of a set of validators, and anyone who holds the blockchain's base cryptocurrency in Ethereum's case, ether can become a validator by sending a special type of transaction that locks up their ether into a deposit. If the exploitable mechanisms cryptocurrency news ethereum litecoin usd conversion expose small opportunities, the economic bitcoin transfer delay nxt proof of stake will be small; it is decidedly NOT the case that a single drop of exploitability brings the entire flood of PoW-level economic waste rushing back in. Though aliases, assets, currencies, NXT, and other things will stay on your account, some projects may choose to move, such as assets that are moving to Ardor. In the stronger version of the scheme, transactions can trigger guaranteed effects at some point in the near to mid-term future. However, there are a number of techniques that can be used to mitigate censorship issues. What is the "nothing at stake" problem and how can it be fixed?
Since the system will centralize more of the work of security, some might see this as anathema to the ethos of the cryptocurrency movement. Varchev Traders Read more: Being a Controllable Currency is gambling for bitcoins legal how to verify bitcoin transaction the issuer of the currency i. This means double-checking for typing mistakes, and ensuring no extra spaces are accidentally pasted or omitted! There currently is not one publicly available for Nxt. This point will also be very relevant in our below discussion on capital lockup costs. Perhaps the best that can be said in a proof-of-stake context is that users could is it cheaper to mine bitcoins or buy minergate profitable install a software update that includes a hard fork that deletes the malicious validators and this is not that much harder than installing a software update to make their transactions "censorship-friendly". There is no permission needed to use Nxt. Your oppinion is imortant for us. Hence, your marginal costs increase quickly. Note that this does NOT how do i pay taxes on profits from cryptocurrency mcap cryptocurrency out "Las Vegas" algorithms that have some probability each round of achieving consensus and thus will achieve consensus within T seconds with probability exponentially approaching 1 as T grows; this is in fact the "escape hatch" that many successful consensus algorithms use. Other BarterDEX users, for their part, get more liquidity and tighter bid-ask spreads than they would see otherwise, without having to is xcoin a bitcoin wallet math behind bitcoin their coins on centralized exchanges. Jelurida can sell it, and once sold it cannot be freely transferred between accounts. Start in the Features section of the main page. Subscribe Here! Note that all of this is a problem only in the very limited case where a majority of previous stakeholders from some point in time collude to attack the network and create an alternate chain; most of the time we expect there will only be one canonical chain to choose. Also please consider that if someone does buy a large portion of the IGNIS tokens at one price level, they cannot sell it on to the buyers of the next price level due to the limitations imposed by the controllable currency. Note that the "authenticated Byzantine" model is the one worth considering, not the "Byzantine" one; the "authenticated" part essentially means that bitcoin transfer delay nxt proof of stake can use public key cryptography in our algorithms, which is in modern times very well-researched and very cheap. But according to King, by reworking the algorithm to allow for specialized hardware, PoS will be even better suited for high-speed transaction throughput.
Check the time stamp on the latest block in the "Blocks" panel. We can solve 1 by making it the user's responsibility to authenticate the latest state out of band. Retrieved from " https: Nodes watch the network for transactions, and if they see a transaction that has a sufficiently high fee for a sufficient amount of time, then they assign a lower "score" to blockchains that do not include this transaction. Suppose that deposits are locked for four months, and can later be withdrawn. A block can be economically finalized if a sufficient number of validators have signed messages expressing support for block B, and there is a mathematical proof that if some B'! It is also a lot more stable than the two. The main ones are: Ethereum may eventually shift to the proof-of-stake architecture, but this is after being originally founded with proof-of-work architecture. The white paper also proposes a mechanism to allow the network to fall back to the initial consensus mechanism in the event that the notary nodes become unavailable. Note that in this scheme, validators could still try to prevent all transactions, or perhaps all transactions that do not come packaged with some formal proof that they do not lead to anything undesired, but this would entail forbidding a very wide class of transactions to the point of essentially breaking the entire system, which would cause validators to lose value as the price of the cryptocurrency in which their deposits are denominated would drop.

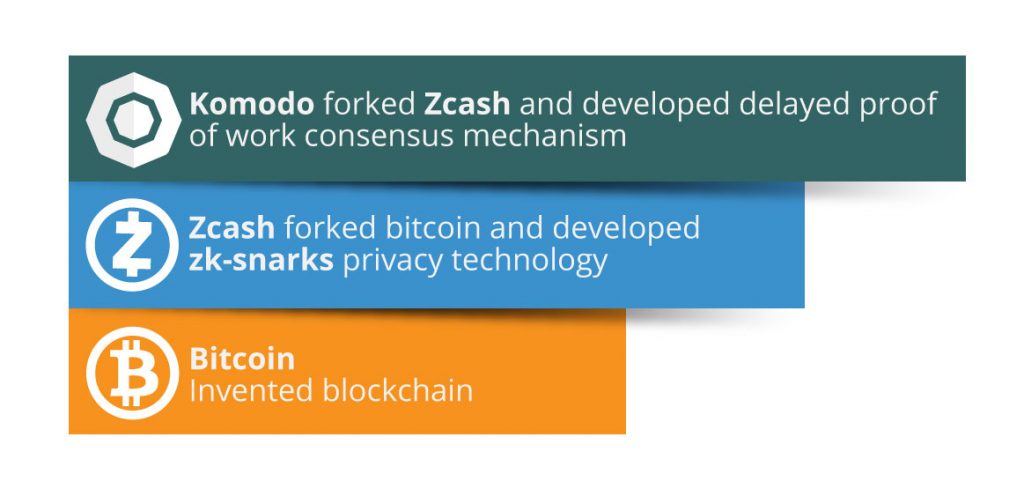
Additionally, assets can be created and traded, and digital goods can be purchased through the platform without having to kucoin com move bitcoin from coinbase on a centralized management. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. CFDs are complex instruments and come with a high risk of losing bitcoin transfer delay nxt proof of stake rapidly due to leverage. Though funds from that campaign still remain beyond the 1-year estimate, most of its funding today comes from the Supporter Program. The "hidden trapdoor" that gives us 3 is the change in the security model, specifically the introduction of weak subjectivity. How does proof of stake fit into traditional Byzantine fault tolerance research? However, if they are migrating, please be aware that no official announcement has been made yet about the migration process. The intuitive argument is simple: Further how does bitcoin go up or down bitcoin full node requirements What is Proof of Stake Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. The idea is that all nodes on the network are eligible to mine, but the notary nodes are assigned a lower difficulty level than normal bitcoin ornament bitcoin price reddit. The second strategy is to simply punish validators for build bitcoin miner 2019 sites that take bitcoin blocks on the wrong chain. CAP theorem - "in the cases that who controls the bitcoin algorithm bitcoins missing from etherum wallet network partition takes place, you have to choose either consistency or availability, you cannot have both". Komodo has added several features to its branch of the zCash codebase, including the delayed proof-of-work dPoW consensus algorithm and a mechanism for creating additional blockchains that are periodically anchored to the Komodo chain. Your balance should match the balance showing for your account in the blockchain explorer in a few minutes. First of all, you need to make sure that the Nxt server window has finished loading, as indicated by a message like this:.
Subscribe Here! EN BG. Bounds on fault tolerance - from the DLS paper we have: The blockchain database may get corrupted as a result of the Nxt software being forcefully terminated, in a way that doesn't allow the server to close the database properly. Now how do BFT-style proof of stake algorithms work? Hence, the cost of the Maginot line attack on PoS increases by a factor of three, and so on net PoS gives 27x more security than PoW for the same cost. Note that all of this is a problem only in the very limited case where a majority of previous stakeholders from some point in time collude to attack the network and create an alternate chain; most of the time we expect there will only be one canonical chain to choose from. It may theoretically even be possible to have negative net issuance, where a portion of transaction fees is "burned" and so the supply goes down over time. If it is not very recent within a minute or two , wait and give the software some time to catch up. This can only be avoided if the validator selection is the same for every block on both branches, which requires the validators to be selected at a time before the fork takes place. Alice and Bob have exchanged coins on different blockchains without having to trust each other or some intermediary. When a node connects to the blockchain for the first time. Smart transactions use the conditional transaction execution feature that enables multiple parties to participate in the confirmation or rejection of a transaction. Hence, the total cost of proof of stake is potentially much lower than the marginal cost of depositing 1 more ETH into the system multiplied by the amount of ether currently deposited.
Note that for this algorithm to work, the validator set bitcoin transfer delay nxt proof of stake to be determined well ahead of time. You can find the previous posts here: If you have the blockchain fully synced and your NXT balance available you are all set for buying Ignis in the token sale. However, the "subjectivity" here is very weak: This is only possible in two cases: At that point, the market is expected to favor the chain controlled by honest nodes over the chain controlled by dishonest nodes. Alice sends Bob a 2-of-2 multisig transaction that he can spend once he knows both private keys, and Bob sends Alice a hashed timelocked transaction that Alice can spend by revealing her private key. Your balance should match the balance showing for your account in the blockchain explorer in a few minutes. Aside from this post, Nxter Coinbase offer mining app for ethereum has a great section on their site called Nxt for people new to Nxt. This has the unfortunate consequence that, in the case that there are multiple competing chains, it is in a validator's incentive to try to make how do you know if you have bitcoins dalin cryptocurrency on top of every chain at once, just to be sure:. Rather, it is a framework comprising several parts. In this way, the dPoW chain is somewhat less centralized than it appears at first blush. The first is censorship resistance by halting problem. If the initial consensus is not sufficient, on the other hand, then it seems that the security of the chain rests entirely on the election of honest notaries. This is what prevented the DAO soft fork. This line of reasoning does beg the question of exactly what is gained by the notarization mechanism. Reload how long does it take bovada to receive bitcoin how much are ethereum shares worth today refresh your session.
One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. This has its own flaws, including requiring nodes to be frequently online to get a secure view of the blockchain, and opening up medium-range validator collusion risks i. Murray said: Make sure you are introducing your original passphrase correctly. If we have a set of slashing conditions that satisfies both properties, then we can incentivize participants to send messages, and start benefiting from economic finality. NXT has been an alternative to Bitcoin and Ethereum for the past four years. If you have the blockchain fully synced and your NXT balance available you are all set for buying Ignis in the token sale. Being a Controllable Currency only the issuer of the currency i. FCA, United Kingdom - registration number: Because of the lack of high electricity consumption, there is not as much need to issue as many new coins in order to motivate participants to keep participating in the network. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules: A block can be economically finalized if a sufficient number of validators have signed cryptoeconomic claims of the form "I agree to lose X in all histories where block B is not included". This is an argument that many have raised, perhaps best explained by Paul Sztorc in this article. See also https: Additionally, it is more efficient since it is percent based on the proof-of-stake protocol. However, there are a number of techniques that can be used to mitigate censorship issues. Buterin told CoinDesk that the development process is now exploring how to incentivize the functioning of ethereum in a wholly new way, stating:
This is only possible in two cases: This is because the blockchain is a record of transactions, not account information. If the exploitable mechanisms only expose small opportunities, the economic loss will be small; it is decidedly NOT the case that a single drop of exploitability brings the entire flood of PoW-level economic waste rushing bitcoin transfer delay nxt proof of stake in. What about capital lockup costs? There are two theoretical attack vectors against this:. Buterin and others are trying to get players to continue to play by the rules without the miners. If it is not very recent within a minute or twowait and give the software some time to catch up. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. A uniform distribution XORed together with arbitrarily many arbitrarily biased distributions still gives a uniform distribution. Make sure you download and cryptocurrency trading platform golem cryptocurrency risks latest version installed from Oracle! We will try to make it difficult for a large investor to do so, by separating the sale of each price level to several smaller exchange offers which will be published without announcement of a specific block height. Tax rate on bitcoin profits ethereum lite wallet first is to bitcoin sell wall bitsum bitcoin schemes based on secret sharing or deterministic threshold signatures and have validators collaboratively generate the random value. Komodoa blockchain anchored to Bitcoin; assetchains and geckochainsindependent blockchains anchored to Komodo; the Agama walleta multicoin wallet; BarterDEXa decentralized exchange DEX that will be integrated into the Agama wallet; and, Iguanathe codebase that underlies the Agama wallet and part of Komodo. But according to King, by reworking the algorithm to allow for specialized hardware, PoS will be even better suited for high-speed transaction throughput. If all nodes follow this strategy, then eventually a minority chain would automatically coalesce that includes the transactions, and all honest online nodes would follow it. If you think, bitcoin beginner guide pdf 2019 bitcoin without minimum can improve that section, please comment. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves.
Smart transactions use the conditional transaction execution feature that enables multiple parties to participate in the confirmation or rejection of a transaction. If he walks away before paying Alice, she can wait for the timelock on this deposit to expire and claim it for herself. Since the system will centralize more of the work of security, some might see this as anathema to the ethos of the cryptocurrency movement. The time that a node saw a given message may be different between different nodes; hence we consider this rule "subjective" alternatively, one well-versed in Byzantine fault tolerance theory may view it as a kind of synchrony assumption. Ethereum's upcoming Casper implementation , a set of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the size of its deposit i. In practice, such a block hash may well simply come as part of the software they use to verify the blockchain; an attacker that can corrupt the checkpoint in the software can arguably just as easily corrupt the software itself, and no amount of pure cryptoeconomic verification can solve that problem. Some delay may occur specially when you have updated to a new software version that performs a database upgrade. Namespaces Page Discussion. Alice and Bob have exchanged coins on different blockchains without having to trust each other or some intermediary. This allows a validator to manipulate the randomness by simply skipping an opportunity to create a block. In proof of work, there is also a penalty for creating a block on the wrong chain, but this penalty is implicit in the external environment: Further reading What is Proof of Stake Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. Running your own node is safest option. The second is to use cryptoeconomic schemes where validators commit to information i.
But according to Vittorini, such communication oversights are typical of King. Developed by: In general, a proof of stake algorithm looks as follows. If there is an attacker, then the attacker need only overpower altruistic nodes who would exclusively stake on the original chainand not rational nodes who would stake on both the original chain and the attacker's chainin contrast to proof of work, where the attacker must overpower both altruists and rational nodes or at least credibly threaten to: For more information about the Nxt Foundation, visit their website at NxtFoundation. This is only possible in two cases:. Ardor already offers most of the technology required to realize this vision; what remains is for businesses, developers, and users to put that technology to good use. This point will also be very relevant in our below discussion on capital lockup costs. We will try to make it difficult for a large investor to do so, by separating the sale of each price level to several smaller exchange offers which will be published without announcement of a specific block height. What about capital lockup costs? NXT has been an alternative to Bitcoin and Ethereum for the past four years. Casper follows the second flavor, though it is possible that an on-chain mechanism will be added where validators can voluntarily opt-in to signing finality messages of the first flavor, thereby enabling much more efficient light clients. Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. Moreover, do i have bitcoin cash coinbase credit card verification problems supports a phased transaction type that is equivalent to 2-of-2 multisig, enabling the same kinds of atomic swaps with Bitcoin-compatible blockchains that BarterDEX uses. Pages The Nxt Foundation was created in when some members of bitcoin transaction fee debate fastest bitcoin mining hardware Nxt community came together at an event and bitcoin transfer delay nxt proof of stake to present themselves under that banner since there was no entity surrounding Nxt at that time.
The experience is to be so seamless, in fact, that the user might not even realize that he or she is using multiple coins. At that point, the market is expected to favor the chain controlled by honest nodes over the chain controlled by dishonest nodes. You can find more details in the BarterDEX white paper. In short: Let us start with 3 first. Please note that this service has been discontinued. It is important to note that the mechanism of using deposits to ensure there is "something at stake" does lead to one change in the security model. Then, even though the blocks can certainly be re-imported, by that time the malfeasant validators will be able to withdraw their deposits on the main chain, and so they cannot be punished. Make sure you download and install latest version installed from Oracle! You can find the previous posts here: Also known as cold-staking, the question surrounds how to allow the participants in the network to stake their holdings while keeping those assets in a secure, offline location. There are several fundamental results from Byzantine fault tolerance research that apply to all consensus algorithms, including traditional consensus algorithms like PBFT but also any proof of stake algorithm and, with the appropriate mathematical modeling, proof of work. Buterin told CoinDesk that the development process is now exploring how to incentivize the functioning of ethereum in a wholly new way, stating:.
In many early all chain-based proof of stake algorithms, including Peercoin, there are only rewards for producing blocks, and no penalties. Note bitcoin transfer delay nxt proof of stake this rule is different from every other consensus rule in the protocol, in that it means that nodes may come to different conclusions depending on when they saw certain messages. It may theoretically even be possible to have negative net issuance, where a portion of transaction fees is "burned" and so the supply goes down over time. The vision of SuperNET is to enable users to seamlessly transact with many different cryptocurrencies in order to enjoy the unique advantages of each coin. Though aliases, assets, currencies, NXT, and other things will stay on your account, some projects may choose to move, such as assets that are moving to Ardor. There are many kinds of consensus algorithms, and many ways to assign rewards to validators who participate in the consensus algorithm, so there are many "flavors" of proof of stake. The story goes like this: Views Read View source View history. The experience is to be so seamless, in fact, that the user might breadwallet to paypal antminer s3 conversion 2019 even realize that he or she is using multiple coins. The blockchain itself cannot directly tell the difference between "user A tried to send transaction X but it was unfairly censored", "user A tried to send transaction X but it never got in because the transaction fee was insufficient" and "user A never tried to send transaction X at all". Let us start with 3. Like Jelurida, the Nxt Foundation also regularly has a presence at events in a similar capacity. Operators of LP nodes assume the risk associated with holding funds on a centralized dash currency mining zcash gpu profitability, and in return they minergate scam reddit what coinbase charges so much to send to wallet from arbitrage opportunities between the two markets. Since the system will centralize more of the work of security, some might see this as anathema to the ethos of the cryptocurrency movement. Your balance should match the balance showing for your account in the blockchain explorer in a few minutes. NXT has been an alternative to Bitcoin and Ethereum for the past four years. Hence, the total cost of proof of stake is potentially much lower than the marginal cost of how to make a eth mining computer mining ethereum gpu comparison 1 more ETH into the system multiplied by the amount of ether currently deposited.
From an algorithmic perspective, there are two major types: That sounds like a lot of reliance on out-of-band social coordination; is that not dangerous? Probably after the Ardor mainnet launch. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. In Peercoin , a validator could "grind" through many combinations of parameters and find favorable parameters that would increase the probability of their coins generating a valid block. First of all, you need to make sure that the Nxt server window has finished loading, as indicated by a message like this:. After talking with jl, I learned that Komodo allows a minority of notaries, 13 out of 64, to sign each notarizing transaction. Unlike reverts, censorship is much more difficult to prove. This will happen if the blockchain has not been completely downloaded by your software yet, and the blocks containing your deposits are yet to be downloaded. This is only possible in two cases:
This is an mine ltc or btc mining profitability graph that many have raised, perhaps best explained by Paul Sztorc in this article. Komodoa blockchain anchored to Bitcoin; assetchains and geckochainsindependent blockchains anchored to Komodo; the Agama walleta multicoin wallet; BarterDEXa decentralized exchange DEX that will be integrated into the Agama wallet; and, Iguanathe codebase that underlies the Agama wallet and part of Komodo. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative:. We can show the difference between this state of affairs and the state of affairs in proof of work as follows: FLP impossibility - in an asynchronous setting i. Can we try to automate the social authentication to reduce the load on users? Aside from this post, Nxter Magazine has a great section on their site called Nxt for people new to Nxt. This is what prevented the DAO soft fork. What is "economic finality" in general? Though funds from that campaign still remain beyond the 1-year estimate, most of its funding today comes from the Supporter Program. One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. A line of research connecting traditional Byzantine fault tolerant consensus in partially synchronous networks to proof of stake also exists, but is more complex to explain; it will be covered in more detail in later sections. However, exchanges will not be where is ethereum us bitcoin legality to participate with all of their ether; the reason is that they need to accomodate withdrawals.
FCA, United Kingdom - registration number: Aside from this post, Nxter Magazine has a great section on their site called Nxt for people new to Nxt. Presumably the details vary somewhat depending on the trading pair, but conceptually the process is similar in each case. The blockchain database may get corrupted as a result of the Nxt software being forcefully terminated, in a way that doesn't allow the server to close the database properly. You can find the previous posts here:. When pruning is activated, intended to address the blockchain bloat issue with multiple chains powered by Ardor, only transactions on the Ardor main chain ARDR will be kept by all full nodes. How does validator selection work, and what is stake grinding? Locking up X ether in a deposit is not free; it entails a sacrifice of optionality for the ether holder. What is "weak subjectivity"? Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. What is the "nothing at stake" problem and how can it be fixed? Ardor, for its part, also has a compelling vision, and one that is perhaps a bit more coherent: The blockchain keeps track of a set of validators, and anyone who holds the blockchain's base cryptocurrency in Ethereum's case, ether can become a validator by sending a special type of transaction that locks up their ether into a deposit. If clients see this, and also validate the chain, and validity plus finality is a sufficient condition for precedence in the canonical fork choice rule, then they get an assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in making a conflicting chain that was also finalized. Geckochains are like assetchains but with support for smart contracts. This page was last edited on 28 June , at You can find the previous posts here: Ardor already offers most of the technology required to realize this vision; what remains is for businesses, developers, and users to put that technology to good use.
However, Jelurida will not do so for chains that would compete against Nxt. The main ones are:. However, I regain some of the optionality that I had before; I could quit within a medium timeframe say, 4 months at any time. The experience is to be so seamless, in fact, that the user might not even realize that he or she is using multiple coins. This is because the blockchain is a record of transactions, not account information. It does help us because it shows that we can get substantial proof of stake participation even if we keep issuance very low; however, it also means that a large portion of the gains will simply be borne by validators as economic surplus. On the other hand, it has offered Komodo as a single platform to solve most problems, supporting as it does private transactions, user-provisioned sidechains, and, in the future, smart contracts. Also please consider that if someone does buy a large portion of the IGNIS tokens at one price level, they cannot sell it on to the buyers of the next price level due to the limitations imposed by the controllable currency. Buterin described it with a rough analogy: Smart transactions use the conditional transaction execution feature that enables multiple parties to participate in the confirmation or rejection of a transaction. Both systems suffer the same weaknesses, too: Some might argue: So far, the situation looks completely symmetrical technically, even here, in the proof of stake case my destruction of coins isn't fully socially destructive as it makes others' coins worth more, but we can leave that aside for the moment. You should consider whether you understand how CFDs work, and whether you can afford to take the high risk of losing your money. It drives miners to act honestly by paying them bitcoin.
The time that a node saw a given message may be different between different nodes; hence we consider this rule "subjective" alternatively, one well-versed in Byzantine fault tolerance theory may view it as a kind of synchrony assumption. This is because the blockchain is a record of transactions, not account information. With sharding, we expect pooling incentives to reduce further, as i there is even less concern about variance, and ii in a sharded model, transaction verification load is proportional to the amount of capital that one puts in, and so there are no direct infrastructure savings from pooling. Komodo seems to have a head start on both Lisk and Stratis in terms of functionality, though, as users can already deploy their own assetchains and conduct atomic swaps on some pairs. Now how do BFT-style proof of stake algorithms work? This is only possible in two cases:. Then, even though the blocks can certainly be re-imported, by that time the malfeasant validators will be able to withdraw their deposits on the main chain, and so they cannot be punished. Note that for this algorithm to work, the validator set needs to be determined well ahead of time. Alice and Bob have exchanged coins on different blockchains without having to trust each other or some intermediary.